It takes a few minutes to know you the bad guy?
Author:Leping Public Security Time:2022.07.01
Modern technology brings convenience at the same time
It also makes people lose "privacy"
On the surface you may be in the virtual world
In fact, behind the network cable is
A two of the invisible eyes are peeping at you
.........

01
Inexplicable "important" text message
Although smartphones have blocked us a lot of spam messages, there are still many seemingly "important" text messages, such as "ETC", "XX Bank", "Taobao shops presented small gifts", "XX customer service" ...
Xiaobian reminds: Do not order the website with unknown history in this kind of information. If it is really official, you will call you instead of just passing a text message.
Real case >>
Recently, Mr. Zhai, a resident of Ma'anshan City, received a text message saying that its ETC had been discontinued and needed to be signed again. So Mr. Zhai click on the link in the text message, binds the credit card, and inputs identity information and verification code. Unexpectedly, a few days later, ETC credit card reminded me to spend twice in different places, and nearly 10,000 yuan was stolen. After investigation, these two money entered the account of Renmou, Wuhan City, Hubei Province, and the other stroke flowed into Zhang Moumou, Qianjiang City, Hubei Province. At the time of the incident, Ren Moumou had a record of travel to Qianjiang, Hubei. Subsequently, the police arrested Ren Moumou and Zhang Moumou. After the case, the two explained that the department helped Wang to transfer funds, and Wang used the mobile wallet payment function to enter the mobile phone information into the mobile phone, and swiped through the POS machine. For the purpose of illegal profits, Wang used false text messages to trick the victims to fill in information such as bank cards and ID numbers through the fishing website, and develop offline funds for the victims of the victims. Currently, the case is under further investigation.

02
Personality test, fortune telling website conspiracy
There are many friends who have tested their personality tests and various fortune -telling and fortunes for curiosity. Some websites only need your name and mobile phone number to register, but some websites need to fill in your birth year, month, month, day, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address, address. Wait, a small gift will be given later, and it will not be received if you do not fill in the detailed residence.
Xiaobian reminds: Before participating in such testing activities, please select a credible website and carefully verify the true situation of the other party's website. Do not rush to fill in personal information leakage.
Real case >>
Recently, Ms. Wang Wang saw a fun test advertisement that "test your true age" in the WeChat circle of friends. Camera access permissions, etc. However, a week later, all kinds of spam and various harassment calls came one after another, and Ms. Wang couldn't help it, and then called the police. Police said that many hot Internet fun test mini programs or APPs will be authorized before testing, and then it can access your photos and cameras. Under normal circumstances, there is an ID card, bank card photo, or other personal information content in the mobile phone album. As long as you authorize, it will automatically collect your photos. Criminals will screen your photos and steal important personal information such as your ID card and bank card.

03
The courier list that is "underestimated"
Many people throw the express packaging containing personal information after receiving the courier, but the cases of selling courier single information are common, and those who are fraudulent through express information abound.
Editor's reminder: For recipients, it is necessary to collect courier and destroy the personal information on the courier list in time. Don't easily believe in the so -called customer service, after -sales telephone and text messages. Please contact the seller to verify the officials in time in the case of abnormal order. Happening.
Real case >>
Recently, a business merchant in Yiwu City called the police for help, saying that he received a client that he had received a fraud call several times recently, and it contained accurate personal information. He suspected that someone leaked the information and asked the public security organs to find out the truth. After investigation, the police discovered that the suspect Zhang had made some fast -moving courier numbers to earn some fast outside, and then extended the next family to acquire the face information provided by others. As of being arrested, Li had a total of about 5,000 yuan.

04
Seductive social app
Related data show that China's single population has exceeded 200 million. Due to the fast pace of life, high work pressure, small social circle, etc., young people have become a very common phenomenon in dating and dating through online ways. The registration information leaves the opportunity for criminals. In particular, the income of single women, personal property, work, living conditions, etc. have become the focus of criminals.
Editor's reminder: Be sure to choose a large website with strength and guarantee, fill in personal information with a proper manner, do not easily register the niche and be under the unknown website of VIP trail members.
Real case >>
Recently, Zhengzhou City has cracked a case of extramarital dating and dating online fraud cases. More than 200 criminal suspects were involved in the case, more than 2 million yuan in fraud, and affected more than 10 provinces and more than 7,000 victims across the country. After investigation by the public security organs, since 2017, the fraud group headed by Cai Mouxin, Wang Moumou, etc., has long been in the district, county urban area and urban and rural combinations for illegal interests. Fraud groups specializing in dating and dating fraud crimes. The fraud group adds a large number of "opposite sex" friends in different regions through multiple social software. After deceiving the other party's trust with the guise of marriage and dating, he compiled the reason to deceive the other party to send red envelopes and transfer. 05

Takeaway that was thrown at the door
Nowadays, the vast majority of units are not allowed to send takeaway upstairs. The small tables at the door are set up specifically for takeaway. If the takeaway is not taken in time, the details of the name, telephone, work floor, etc. are exposed. Single information will be "seen".
Xiaobian reminds: Try not to use the real name when clicking takeaway. Be sure to set privacy options. If the unit is not allowed to take the takeaway upstairs, do not write the information too detailed.
Real case >>
Recently, a girl in a city in other provinces was obscene by strange men. It is reported that the man picked up a takeaway order and learned about the girl's identity, phone calling and other information, and then called the girl to deceive him downstairs late at night. It is understood that the takeaway merchants did not desensitize the personal information of the order, and the takeaway riders abandoned the takeaway documents at the elevator. According to the girl: "When I got takeaway, I didn't find the takeaway order, but I didn't think much at that time."
06


Those friends who have been peeped
We usually take selfies, foods, and surroundings in the circle of friends ... but if we are remembered by the "thief", the consequences are unimaginable.
Xiaobian reminded: Please be careful in these things in friends!
1. Train tickets, plane tickets, boarding passes. Most people will code the ID card information, but the QR code or barcode also contain passenger information. For safety reasons, timely destroy;
2. Passport, door key, license plate. This information will leak the specific location where your specific time is, and your life circle;
3. Children's photos, names, and schools, so that you may be deceived, but your child may be tricked.
Real case >>
The information contained in a photo is much more than we think. As long as you take a photo, you can easily master your shooting time, mobile phone model you use, and even the location of the photo! Recently, Xiaobian turned on the camera to take a photo and sent a photo to the computer desktop through WeChat. We can see that the picture information contains very accurate longitude, latitude, and height.
Let's count a few small points behind. The accuracy level is dazzling ... Through some EXIF information analysis software, you can also accurately locate a certain building where you are in the shooting. Then, through high information, combined with the local altitude height, and comparison of information such as maps, the floor where the other party lives. Once, a station B UP master, with a landscape photo provided by fans and analyzing various information, accurately found the specific floor of the photo shooting.
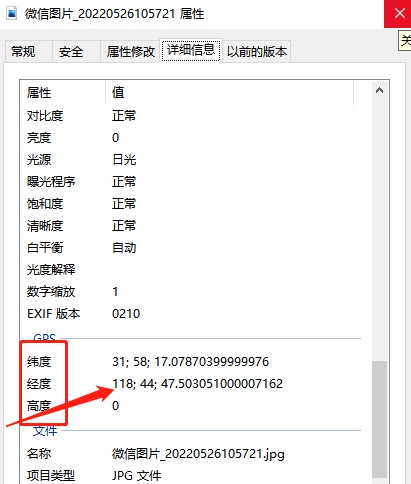
07

"Free wifi" is really free?
Many public places have free WiFi for people to enjoy. What is behind him? The survey results show that these free WiFi need to enter the mobile phone number and fill in the verification code of the return text message before it can be used. Most of his hooligan software invades the user's mobile phone. User information has formed an important part of the gray industry chain.
Editor's reminder: Don't "greedy" free WiFi. As the so -called "gifts for all fate have long been marked in the secret price."
Real case >>
Recently, Ms. Li, a citizen of Jingzhou, went to the bank to prepare for the business. When she querying the balance of the card, she found that more than 10,000 yuan was missing. According to Ms. Li's memories, she had a business trip in the field before. When she visited the mall, she connected a free WiFi to charge 200 yuan. In the end, she did not consume it anymore. “整个过程自己一点都不知情。如果卡内资金变动,我应该会接到短信提醒。”李小姐表示疑惑,以前每次转账都会收到校验码提醒或者支出资金的短信,但这次没有Receive any prompts. Based on this, the bank staff judged that Miss Li may be stolen by hackers when the free WiFi is connected to the free WiFi, and the SMS reminder is also blocked.
Information leak has become a major hidden danger in modern life


The mobile phone does not leave the hand information without hiding
We can't stop the "evil thoughts" of criminals
I only pay attention to small details in life at all times
Wake up as much as possible
In order to give yourself one more layer of protection
Texas Public Security Rong Media Center
Painting/Editor | Zhao Lulu
Blame | Zhao Shuai
Review | Li Jie
- END -
Russian version of McDonald's "Full Moon", happy and worried

Customers pick up meals in the only delicious store. Li Linjia Photo After one mon...
"Old Rules" is not a violation of discipline to block the arrow card

2022 Issue 23 (Total 203)纪 Recently, the China Discipline Inspection and Supervis...