How to prevent telecommunications fraud, these common sense will be given to you!
Author:Linxia Rong Media Center Time:2022.06.28


Frequent fraud methods
Recently, new characteristics have emerged as fraud crimes. Criminals have carefully deployed various means, carefully deployed, deceived the trust of the victims and infringed their property, and seriously disrupted the normal work and production order of the people. The common methods of telecommunications fraud are announced to everyone, please pay attention to prevention.
1. Pretend to be a public prosecutor's staff on the grounds that the victim's identity information was stolen, etc., and asked the victim to transfer money to the "security account" for fraud.
2. Pretend to be fire officers and soldiers and troops to perform fraud with "introduction engineering".
3. Pretend to be a bank customer service, mobile customer service, with points exchange cash as a SMS fraud.
4. WeChat and QQ who posted corporate leaders to perform fraud on corporate financial and accounting staff.
5. Precursing telephone frauds such as maternity subsidies, funeral subsidies, housing subsidies, car purchase subsidies, disabled subsidies, and second -child subsidies.
6. Purchase ticket fraud using false websites, telephones and other methods.
7, "pretending to lead leader" on the grounds of "gift giving" telephone fraud.
8. "Credit and commission" network part -time fraud.
9. Call for a "old friend" to "guess who I am" phone fraud.
10. On the grounds of the detection of drugs for the victim's parcel, he was suspected of drug crimes and asked the victim to transfer money to the "security account" to perform fraud.
11. Pretend to be a bank staff to implement fraud on the grounds of "increasing the credit card quota".
12. SMS fraud on the grounds of "flight cancellation".
13. Send false recruitment advertising fraud.
14. Fraud for fictional stocks.
15. Precurs to acquaintance fraud.
16. Online shopping fraud.
17. False winning information fraud.
18. Use the hit video to download and spread the Trojan virus to perform fraud.
Cleaning of telecommunications network fraud
Unknown calls are hung in time; don't reply to suspicious text messages;
Card numbers and passwords must be kept secret; do not leak identity information;
QQ videos can be faked; carefully checking and not trusting;
Transfer remittances must be cautious; more than 10,000 yuan to the counter;
Pay attention to the pocket; the security of funds is guaranteed;
To verify the arrears notification, be cautious with a large amount of remittances;
Numberless number, do not connect lightly, set up traps of virtual telephones;
The tax refund prize is a scam.
Be careful to travel to the Internet, and the scam means are renovating;
True and false online stores are difficult to distinguish, and they are deceived by accidental shopping;
It is most common to run when it is difficult to check the goods in the second place;
Investment wealth management and stocks are mostly sets of scammers;
The so -called inside story and information are all the measures of others;
The online prize is really ruthless, most of the prizes are notebooks;
You need to handle fees first, and buy a lesson is really expensive;
Preventing the Internet fraud, not greedy and cheap to remember;
Once it is difficult to divide the false and true, 110 consultation is the most assured.
Important reminder: The "National Anti -Fraud Center" APP is a special software for anti -telecommunications network fraud in a "fraud warning, quick reporting fraud, anti -fraud anti -fraud knowledge learning, etc.". In order to improve the ability to prevent telecommunications network fraud, please install and use it as soon as possible!
National Anti -Fraud Center APP operation process
As an artifact to protect the "money bag", first of all, please let me introduce myself. I am the "National Anti -Fraud Center" APP and an app organized by the Criminal Investigation Bureau of the Ministry of Public Security. Telecom network security, establish a channel for reporting the network of telecommunications networks for users, strengthen prevention and publicity, and commit to building a good telecommunications network environment.
In addition, you don't have to worry about leaking personal information in the process of using me, because at the beginning of my birth, I must strictly follow the "Cyber Security Law of the People's Republic of China" and relevant laws and regulations to determine the privacy and security of citizens. Technically and management, I have a reasonable and effective information security technology and management system for me, which can prevent user information from leaking or tampered with, and ensure that your personal information security is safe.
People are a artifact that integrates "fraud warning, quick reporting fraud, anti -fraud and anti -fraud knowledge learning, etc.". The following is the ability of others
1. You can provide you with anti -fraudulent protection for free. When you receive a call, SMS, URL, or installation of suspected fraud apps, you can intelligently identify the identity of scammers and early warning, which greatly reduces the possibility of deception.

2. Report online for illegal and suspicious telecommunications network frauds to provide more anti -scratch clues for public security. In the process of using the mobile phone, if you find suspicious mobile phone numbers, text messages, gambling, fishing websites, scam APP and other information, you can report it in the "I want to report" module, and they will be blocked in time in the background.
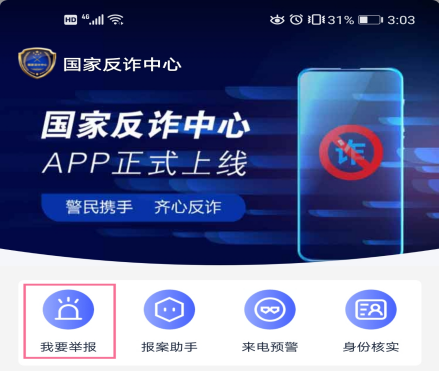
3. Regularly push anti -fraud articles, expose the latest fraud cases, and raise awareness of anti -fraud. At the same time, according to the characteristics of different ages and occupations, the risk index of cheating is tested to prevent problems before they occur.

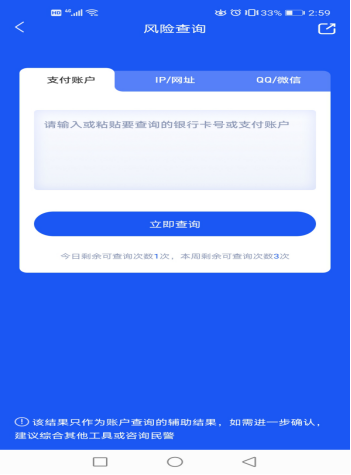
4. Risk query. When involving strange account transfer, you can verify whether the other party's account is involved, including payment accounts, IP URLs, QQ, WeChat, etc., to avoid the risk of cheating funds in time.
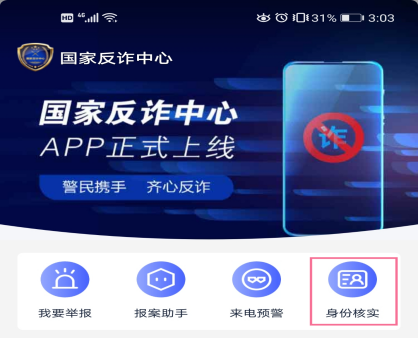
5. Perform real identity verification. When making friends and transfer on social software, verify the authenticity of the other person's identity to prevent the other party from having the identity for fraud.
People are so good
What should I pay attention to when used?
Be sure to remember
01. Real -name verification is required.
02. When providing clues, fingertips, and number labeling functions, you need to verify first.03. Fraud early warning permissions cannot be used to use the early warning function.

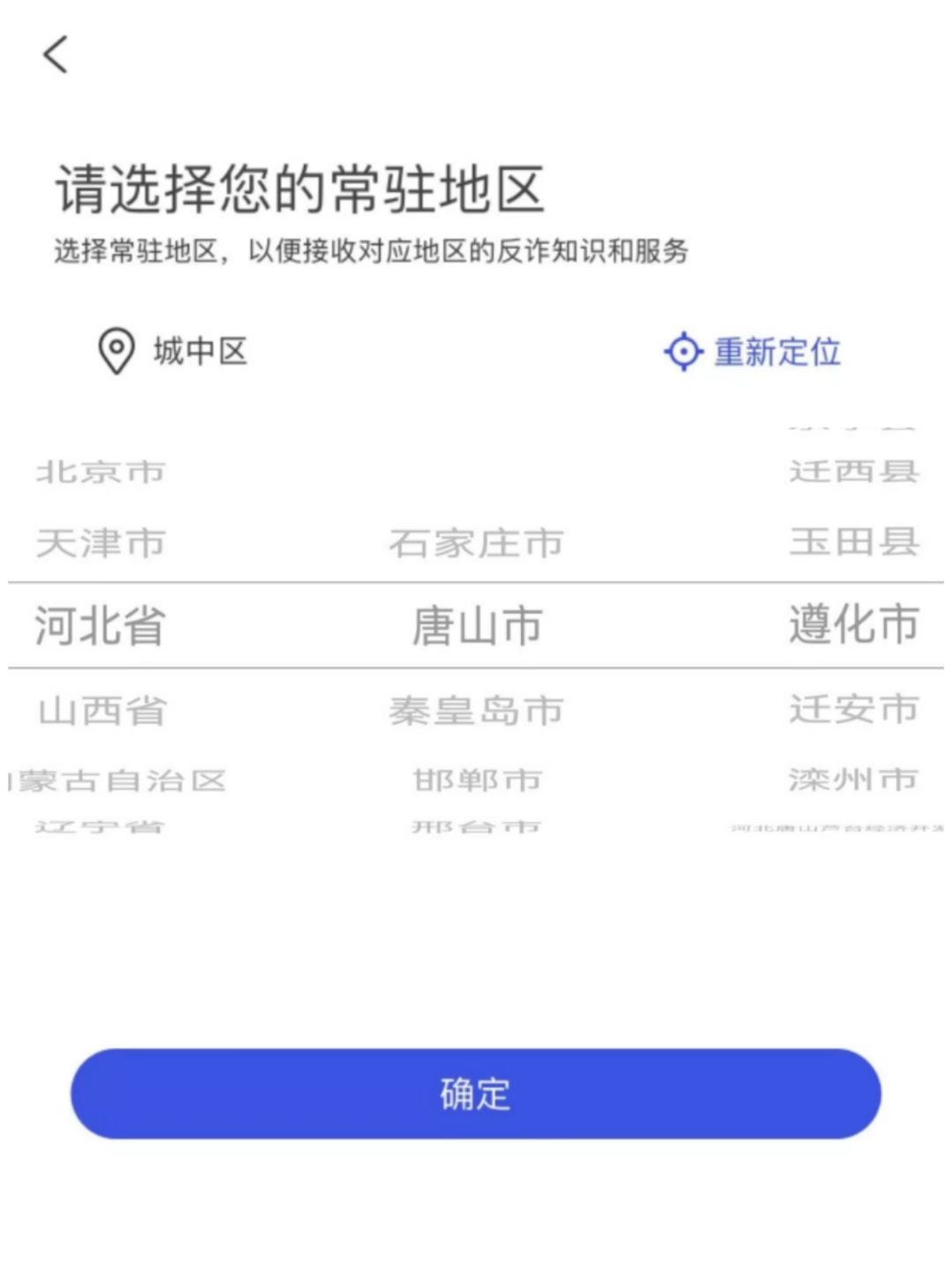
04. You must fill in the "Zunhua City of Tangshan City, Hebei Province" in the area. The detailed address must indicate the town street in detail, and to the house number in detail.

05. Fill in all social communication information, which is conducive to precise early warning fraud information.
06. When using APP, you need to click the "Fraud Early Warning" module to authorize mobile phone permissions, such as "suspended windows", "call records", "photo access", "video access", "access to SMS", "access address book" and so on.allow
Friends who have not installed yet
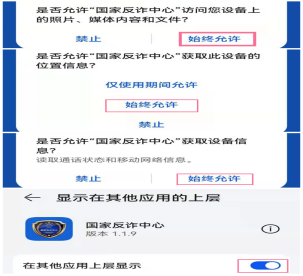
Take it quickly
Let it always
Protect our "money bag"
Source: Longnan Public Security Rong Media Center

Click to share!Point collection!Little like!Click to watch!

- END -
Taizhou: 4,000 people participated, welcoming the party's "20th National Congress"

I and my motherland can not divide a moment when I go wherever I go ... In the sum...
The cadres of the direct unit of Loudi City to the township (street) are held

The cadres of the direct unit of Loudi City to the township (street) are held82 yo...