"Malicious invasion" people pay attention to college students!Lawyer: It may be suspected of crime
Author:Guangdong Communist Youth Leag Time:2022.09.08
Recently, some college students exposed
The online course platform used by myself
Classed by others maliciously
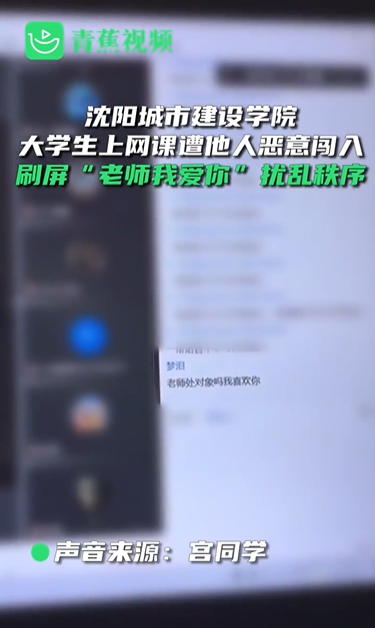
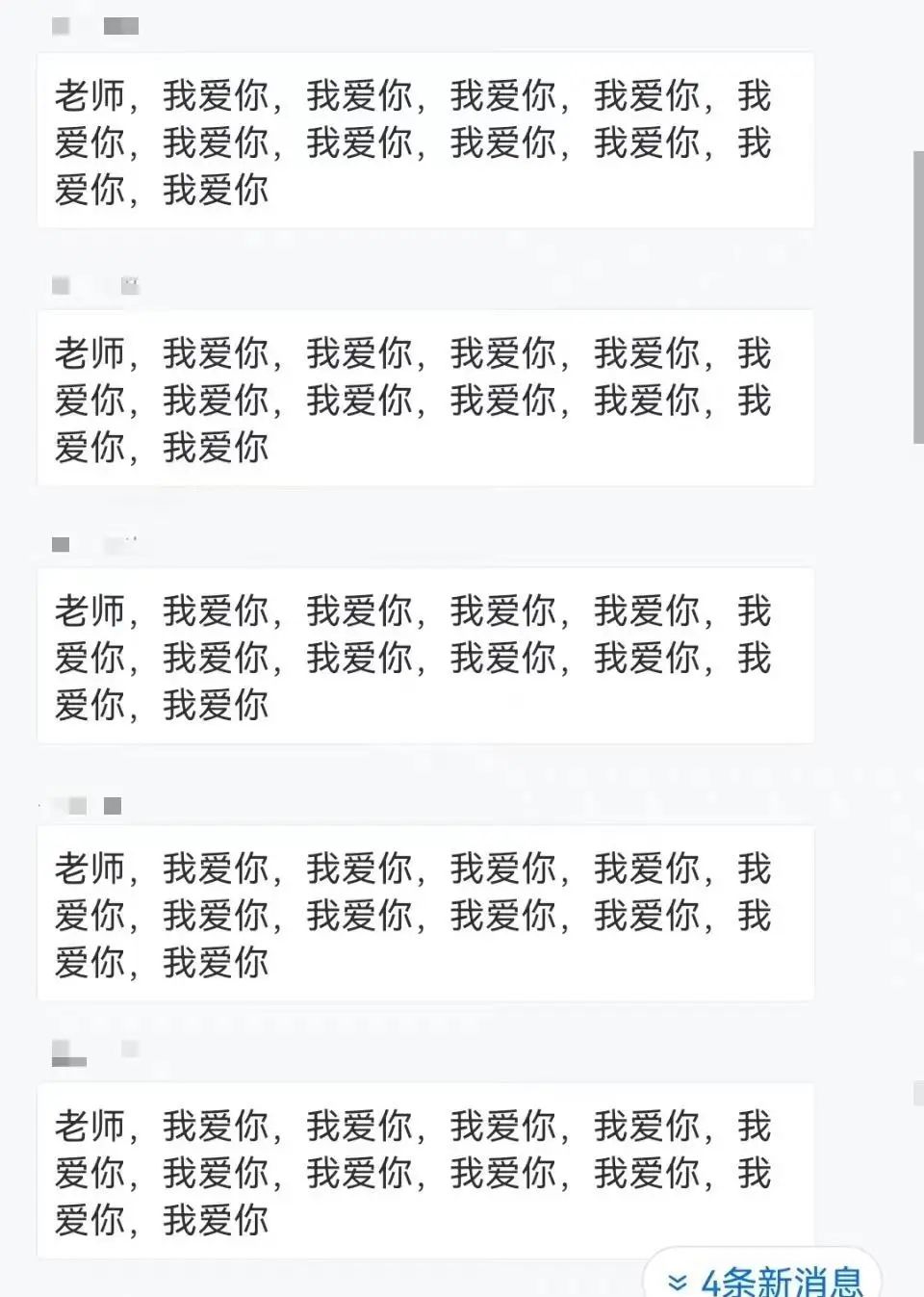
The online class meeting was maliciously brushed "Teacher I love you"
September 5th
Gong classmate said
Discover the meeting during the Internet class
Several strangers
"At first I thought it was a rebuilt classmate didn't care
Subsequently, someone opened the wheat song
And say "I like you" to the teacher. "
Video screenshot. Picture Source | Cover News
Video screenshot. Picture Source | Cover News
The palace classmate expressed his anger
"Teachers are not easy to prepare lessons
Don't respect the teacher
Class order is also very chaotic
They don't want to listen or not
No need to disturb others "


Video screenshot. Picture Source | Cover News
Later, the students also reported to the school,
At present, the school has launched an investigation
According to media reports
In the past few days
Many students who have delayed school
I encountered similar ones during the Internet class
"Internet invasion", its "invasion"
Diverse content and many people
Speak from Kaimai, play songs, swipe screen domineering
Go to the live broadcast of obscene videos and abuse teachers and students
There are many "online classes blasting" groups in the network
It is reported that the behavior of this invasion of the Internet class is called "Internet Class Blast" on the Internet.
According to the Shandong Business Daily, the reporter immediately entered the keywords of the "Internet Class Blast", "Blasting Group" and "Prohibited Network Class" on multiple social platforms, and searched for many similar social groups.
Video screenshot. Picture Source | Cover News
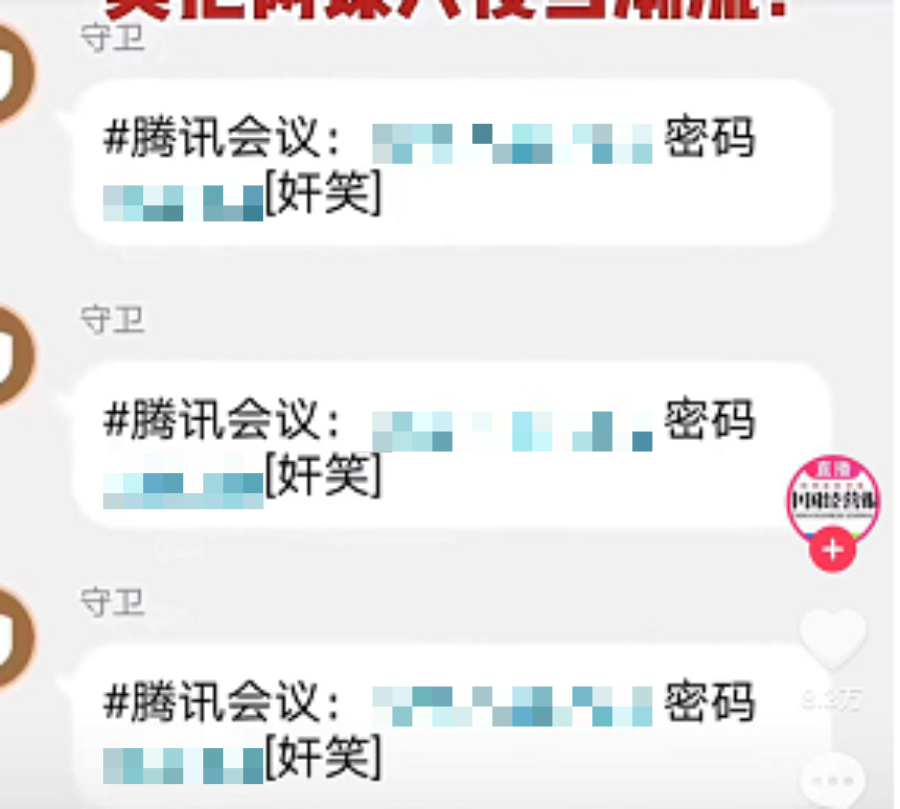
Senior netizen A Xing told reporters, "This" Internet Class Blast "action, generally speaking, insiders will leak the online class time and room number by insiders. The fixed time, collection 'blasting' network lesson, prevent or disturb normal online teaching. "
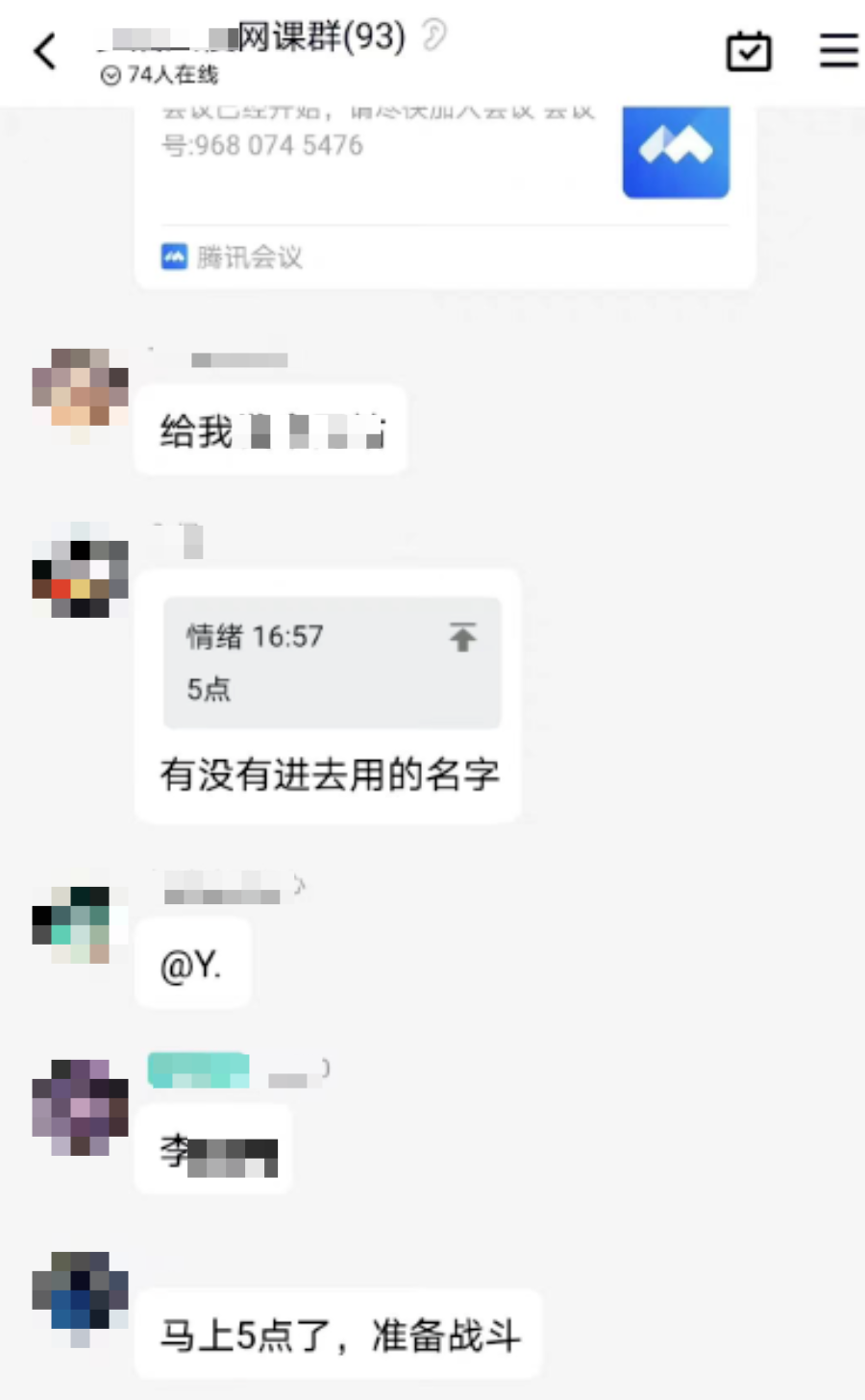
A "Internet Class Blasting" participant said: "Except for some online courses that have no passwords entering randomly, most of the other conference numbers and passwords provided by the students provided by the students."
Video screenshot. Picture Source | Cover News
A Xing said that the form of "online class blasting" actually existed for a long time.
"You can understand it as a" explosion bar "in the early years, which is a kind of cyber violence. Before, it was constantly posting insulting posts, water posts, garbage posts, etc. in the designated post. The order of the post bar, but now it is just to change the position to the online class platform, such as Tencent Classroom, Tencent Conference, Nailing, etc. are the targets of 'invasion'. "A Xing said.
Lawyer: "The Internet is not a place outside the law"
Liu Xiaoyu, a first -level partner and lawyer of Shandong Qiding Law Firm, said:
The network is not a place outside the law. The order of the network space is protected in accordance with the law. Any behavior that interfere with the order of the network space of others in accordance with the law is subject to legal constraints in accordance with the law. In consequences, according to the Criminal Law, its behavior may be suspected of constituing other crimes.
The reporter noticed that there were already online police issues to pay attention to the invasion of the online class:
Common concern! Online classroom "anti -broken" guide
On September 6, the official account of the Tencent Conference published "Common Follow!" Online classroom ‘Prevention’ Guidance. ” Before the meeting, during the meeting, and after the meeting, multiple measures can be taken to ensure the security of online classrooms, improve the quality of teaching, and avoid people from entering the meeting to disturb the class order.
How to avoid the invasion of the online class meeting
Take Tencent Conference as an example
Before the meeting
The Tencent Conference provides a variety of pre -set settings to ensure online class safety, and meet the teaching needs of various scenarios such as classrooms, seminars, and defense.
Method 1
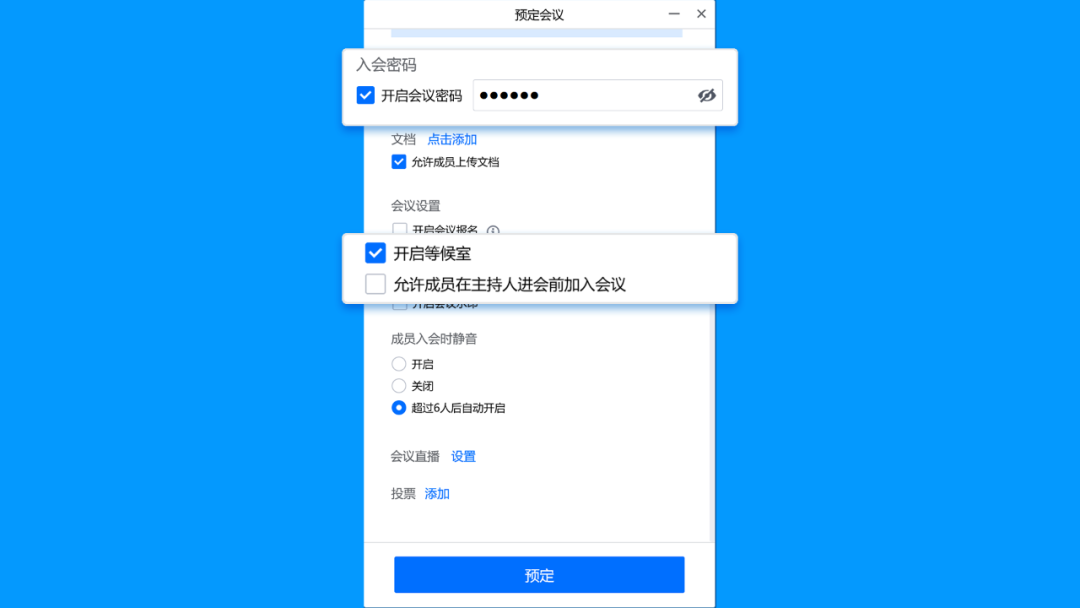
Conference password+waiting room
When a predetermined meeting or using a personal meeting number to launch a fast meeting, the host can set the conference password and open the waiting room to prevent others from entering the classroom by mistake, and can close the "allow members to join the meeting before the host enters the meeting." Setting path: Reservation meeting & opening the conference password, opening the waiting room
Method 2
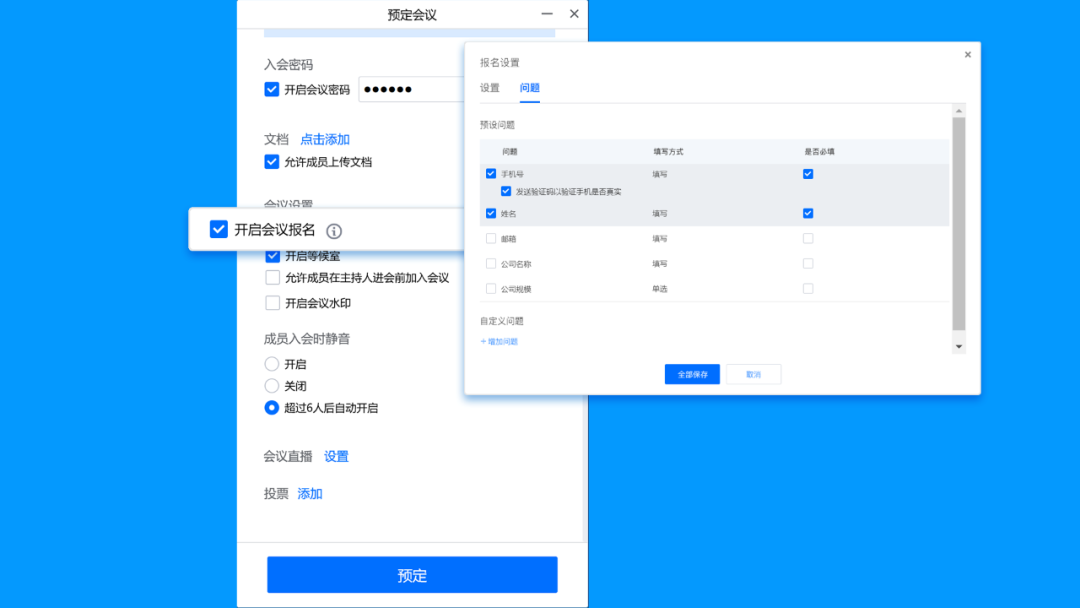
Open the meeting to register
For the closed seminar, in addition to setting the password and the waiting room, the host can also start the registration mode when the scheduled meeting, set the mobile phone number and name as a required item, and set the "send the verification code to verify whether the mobile phone is true" After passing the review, the participants' nicknames will display their names to facilitate the identity of the participants.
Setting path: Reservation meeting & opening meeting registration, setting up registration issues
Method 3
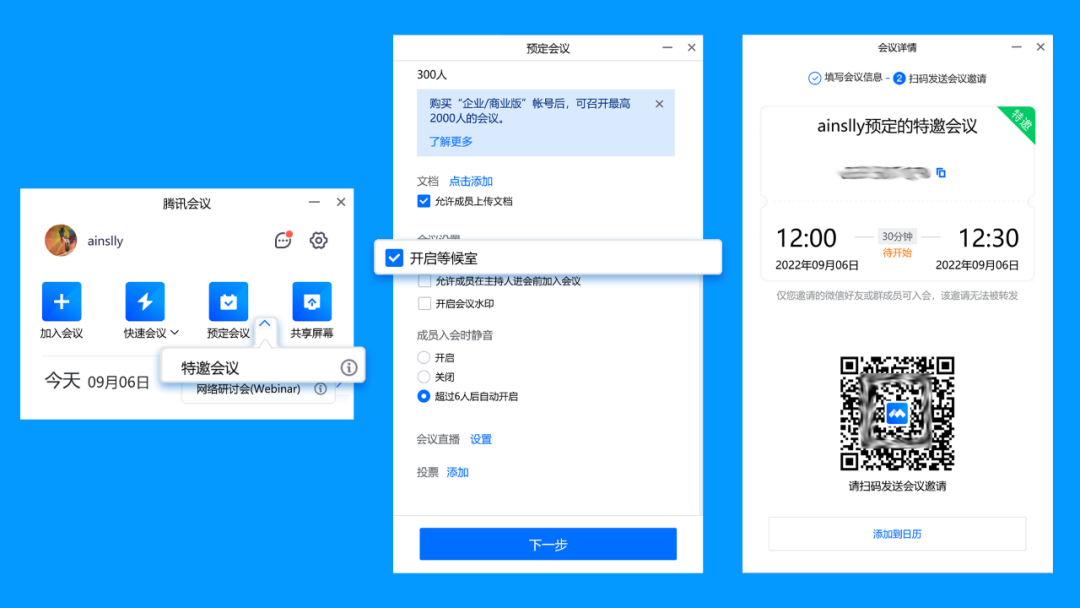
WeChat special invitation meeting
If you have a class or Course WeChat group, you can consider the specially invited meeting of WeChat. Friends or group members invited by the conference reservations can join the meeting, and the conference link forwarding is invalid.
Setting path: Book the meeting, choose the "Special Conference" on the side of the arrows & open the waiting room & forwarded to WeChat group
Meeting
During the meeting, in order to create a good and orderly teaching atmosphere, the host (teachers) can perform the following operations:
01
Manage students sharing screen/annotation permissions
The host can set the shared screen permissions as "all members can share" or "only the host can share", and close the "allowing other members to add interactive annotations" as needed to ensure the order of classroom demonstration.
Setting path: (in the meeting) Sharing screen right arrows & setting sharing permissions; (after opening sharing) Interactive comments on the right arrow & Close "Allowing to allow other members to add interactive annotations"
02
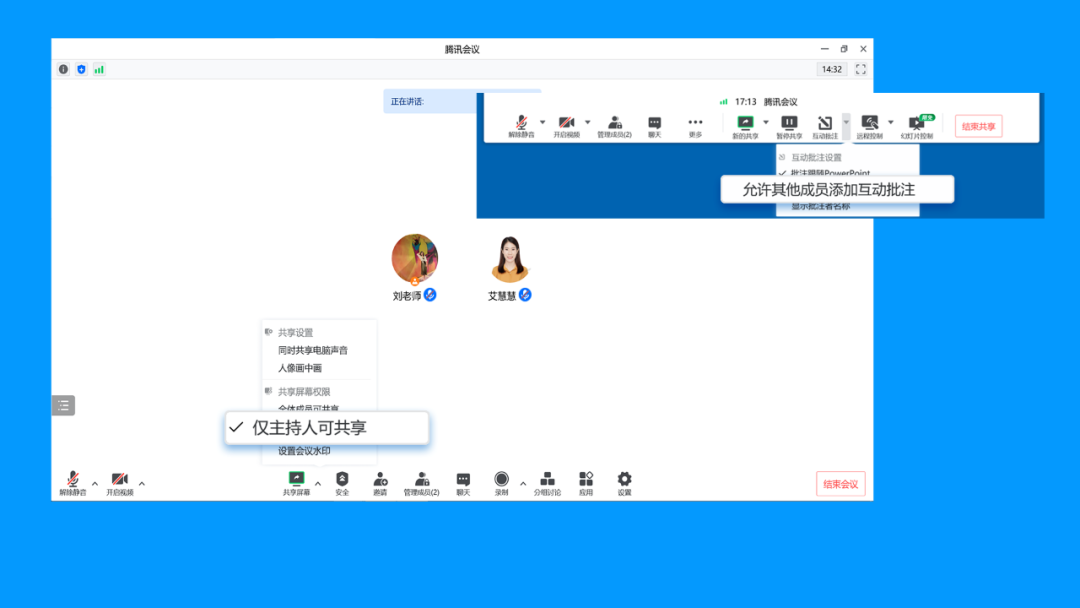
In the meeting, prevent outsiders from being mistakenly entered
When all the students are in place, the host can open the "locking meeting", and others cannot join the meeting at this time. If you find a person who entered the meeting by mistake, you can "move out of the meeting" and set up "the user is not allowed to join the meeting again."
Setting path: (during the meeting) security & locking the meeting, or moved out of members
03
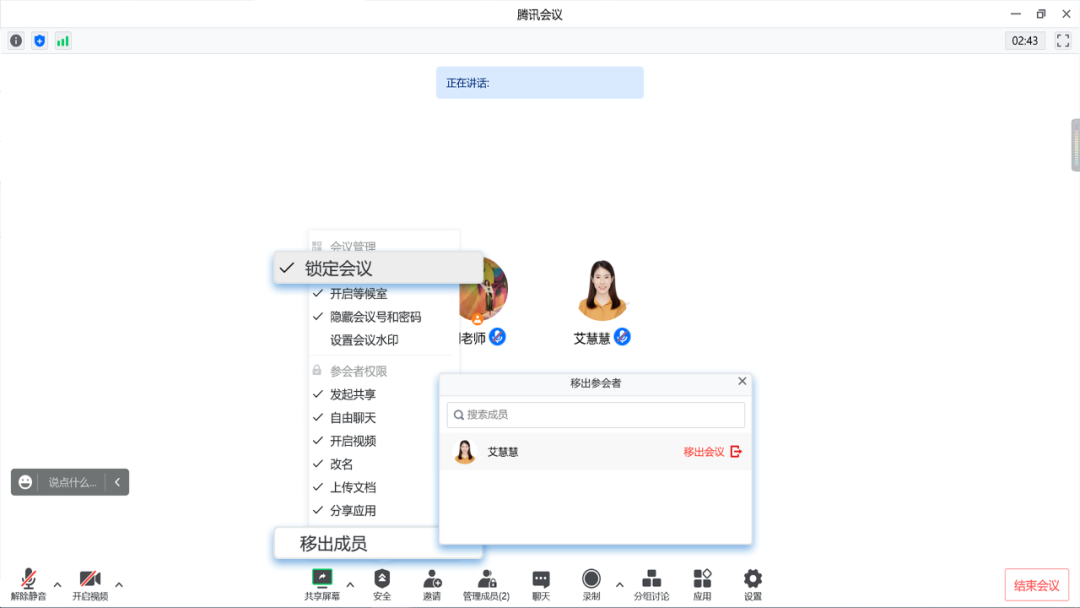
Manage students' speech permissions
In order to prevent students from turning on the wheat by mistake and disrupting the rhythm of the lecture, the host can turn off "allow members to relieve the silence" and start "allow members to raise their hands". When the interactive link, they can communicate with their classmates' speeches.
Setting path: (during the meeting) Management member & more & closure "allow members to relieve the silence" and turn on "allow members to raise their hands" & turn off "allow members to open video" on demand "
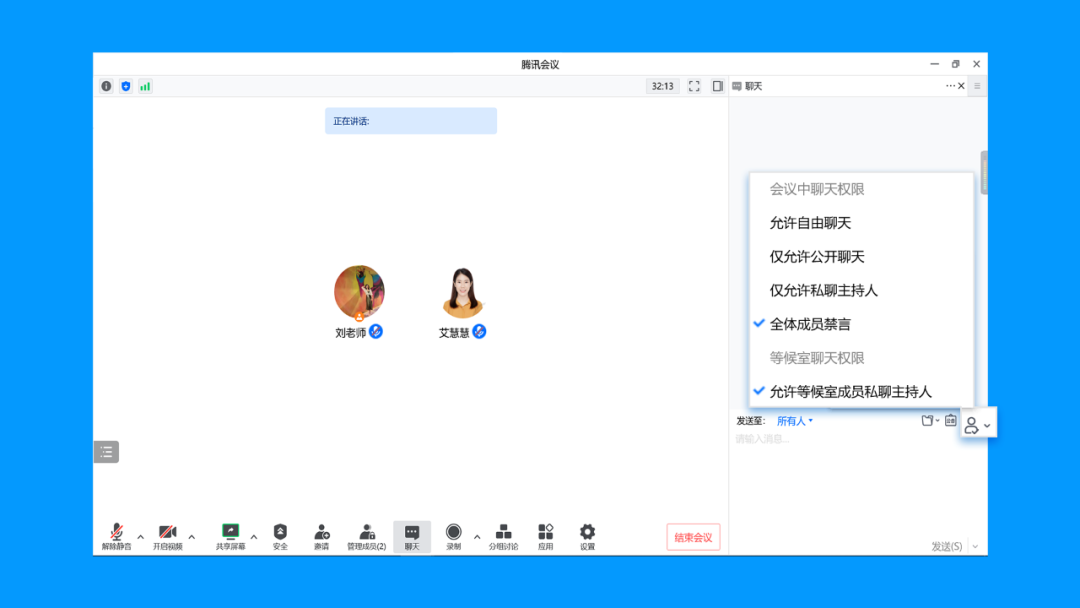
04
Manage the right to chat with students
In order to create a more focused classroom atmosphere, teachers can choose to set up members' chat rights and close free chats to reduce "classroom whispering", or only allow public chat to retain the classroom questions.
Setting path: (in the meeting) Chat & Setting Chat Rights
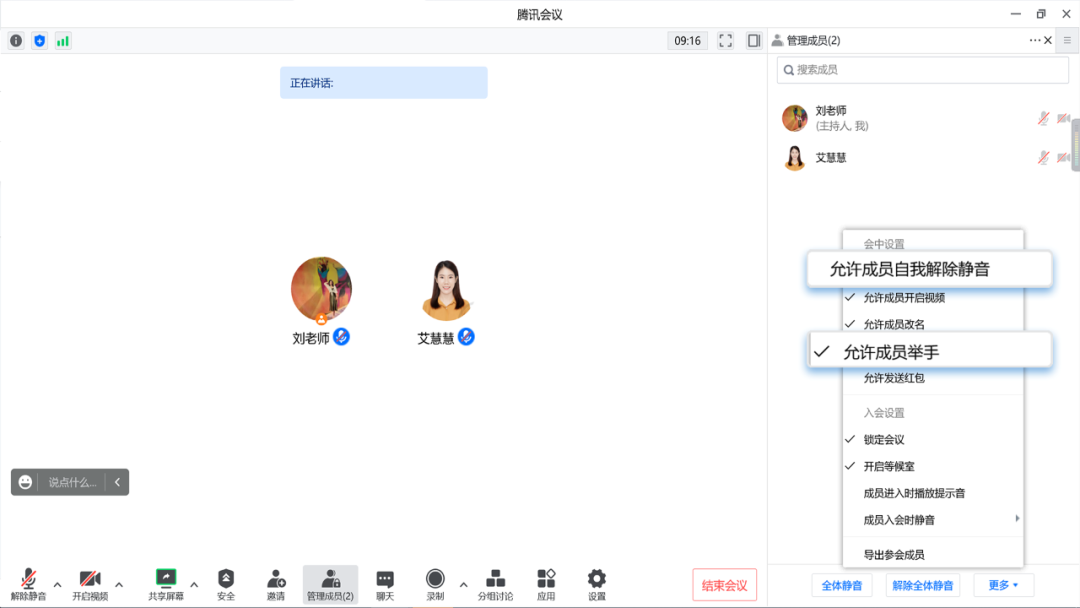
05
Manage other collaborative permissions on demand
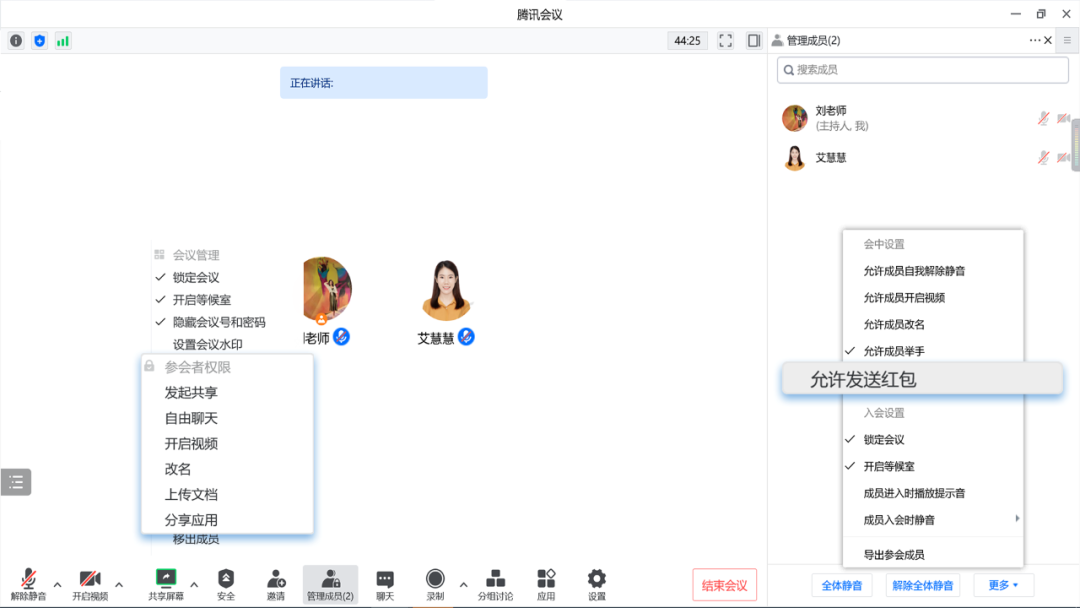
In addition to the above operations, the host can also choose to set up the participating members to modify the nicknames, red envelopes, upload documents, and share applications to make the classroom more orderly.
Setting path: (in the meeting) Safety & Set the authority of the participants; (during the meeting) Management members & more & turn off the "allowable red envelope"
After the meeting
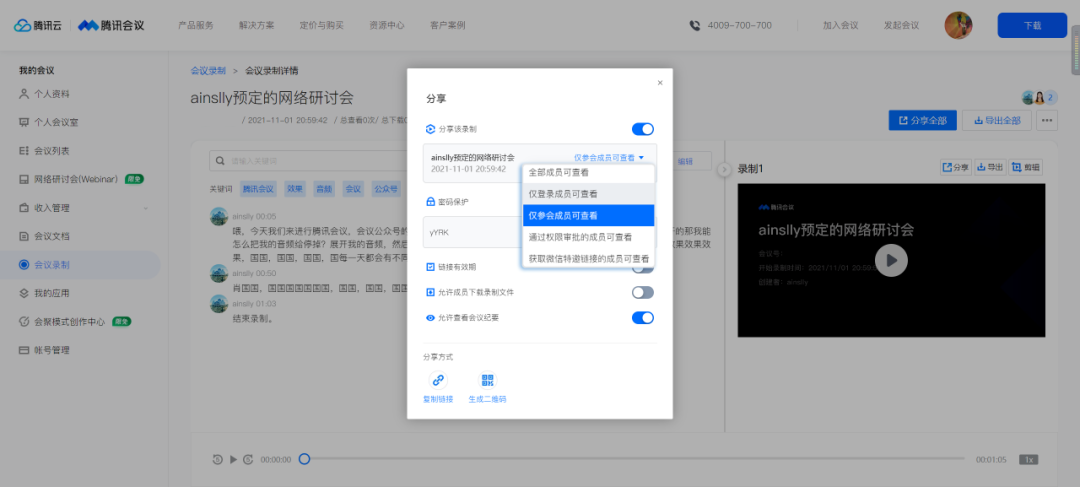
If you turn on cloud recording at the meeting, you can set up cloud recording to view and download permissions after the meeting, so that the students will also protect the scope of the transmission of courseware while reviewing.
Setting path: Official website & Personal Center & Conference Recording & Setting and Downloading Permissions on a recording document
report
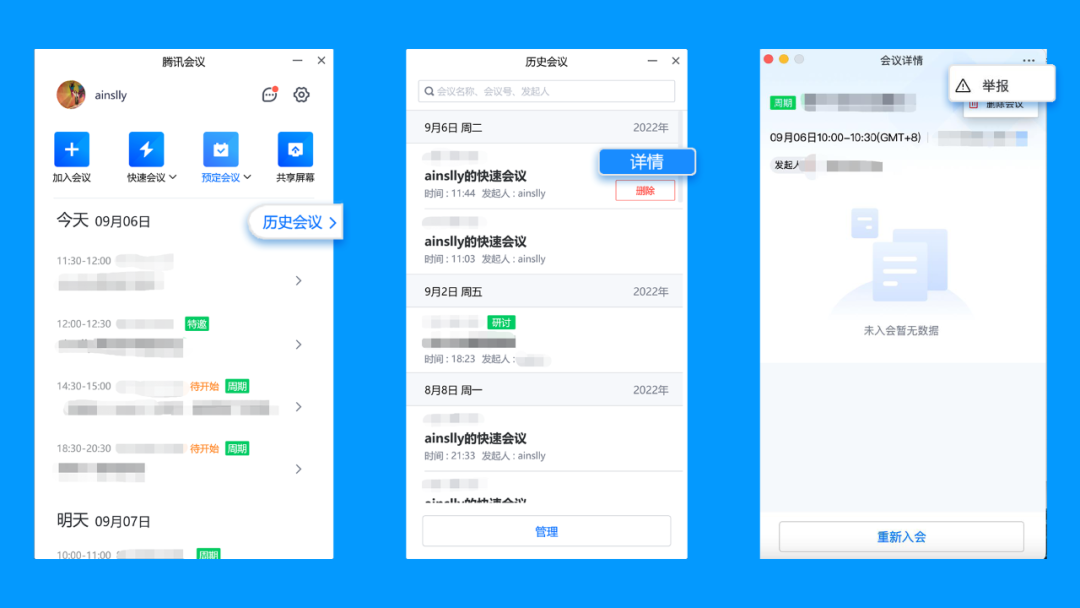
If you find that someone else enters the meeting and interferes with the order of the class, you can report it after the meeting and provide relevant materials to work together to build a green healthy network environment.
Setting path: (after the meeting) Historical Conference & Details & "…" & Report
The Guangdong Communist Youth League comprehensively organizes the China Youth Daily, Shandong Business Daily · Sudao News Network (Reporter Zheng Yannan Zheng Xiaotong), cover news,@Shenzhen Net Police, Tencent Conference, etc.
Edit: Orange
- END -
Shanxi introduced the first entrepreneurial subsidy of college graduates for the first entrepreneurial subsidy of the college graduates of Shanxi

Xinhua News Agency, Taiyuan, June 29 (Reporter Ma Xiaoyuan) The reporter learned f...
Chengdu calm down the property people are busy

Cooperate with the community to conduct a whole nucleic acid test, deliver living ...