Attack the source of the attack: US National Security Agency
Author:Chang'an Street Knowledge Time:2022.09.05
On June 22, Northwest University of Technology issued a statement saying that it was attacked by overseas networks. On September 5, the National Computer Virus Emergency treatment Center issued the "Northwest University of Technology's Investigation Report (one) by the NSA network attack event (one)" (referred to as the "Investigation Report").
The "Investigation Report" disclosed that the initially determined that related attacks originated from the National Security Agency (NSA) "Office of Tailored Access Operation (TAO).
Screenshot source: National Computer Virus Emergency Treatment Center official website
This survey found that in recent years, TAO has implemented tens of thousands of malicious network attacks on China's domestic network targets, and controls tens of thousands of network devices (network server, Internet terminal, network switch, telephone switch, router, and router Firewall, etc.), stole high value data of more than 140GB. TAO uses its network attack weapon platform, "zero -day vulnerability" (0DAY) and its controlled network devices to continue to expand network attacks and scope.
After technical analysis and traceability, the technical team has clarified the network attack infrastructure, special weapons and equipment, and technical tactics used in the TAO attack activities, restores the attack process and stealing documents, and masters the US NSA and its subordinates of China information to China information. Related evidence of the network attack and data theft on the Internet involves 13 people who directly launch cyber attacks in China in the United States, and NSA signed more than 60 contracts signed with US telecommunications operators by covering the company to build a network attack environment. Electronics, electronics, electronics There are more than 170 files.
In the network attack against Northwest University of Technology, TAO used more than 40 different NSA exclusive network attack weapons, continued to attack the stealing of Northwestern Polytechnical University, stealing core technologies such as key network equipment configuration, network management data, operation and maintenance data such as network management, operation and maintenance data of the school data.
Through the analysis of evidence, the technical team has accumulated a total of more than 1,100 attack links that attackers penetrated within Northwestern University of Technology, more than 90 instruction sequences of operation, and positioned multiple stolen networks from the invaded network devices. Equipment configuration files, sniffing network communication data and passwords, other types of logs and key files, and other main details related to attack activities.

According to the "Investigation Report", the network attack weapons used by TAO used in this attack can be divided into four categories:
1. Vulnerability attacks breakthrough weapons, including "shaver", "island" and "sour fox" weapon platform, etc.;
2. Continuously controlled weapons, including "second dating", "nopen", "anger jet", "cunning different criminals", "perseverance of surgical doctors", etc.;
3. Sniffing the stealing weapons, including "drinking tea" and "operations behind the enemy" series of weapons, etc.;
4, concealed firing weapons, including "toast bread".
Based on the relevant technical analysis results and traceability surveys, the technical team initially judged that the network attack operation to the Northwestern Polytechnical University was the US National Security Agency (NSA) Information Intelligence Department (code S) data reconnaissance bureau (code S3). )department. The department was established in 1998, and its power deployment mainly relies on the National Security Agency (NSA) in various password centers in the United States and Europe.
TAO is currently a tactical implementation unit specializing in the implementation of large -scale network attacks on other countries. It is composed of more than 2,000 soldiers and cultural personnel.

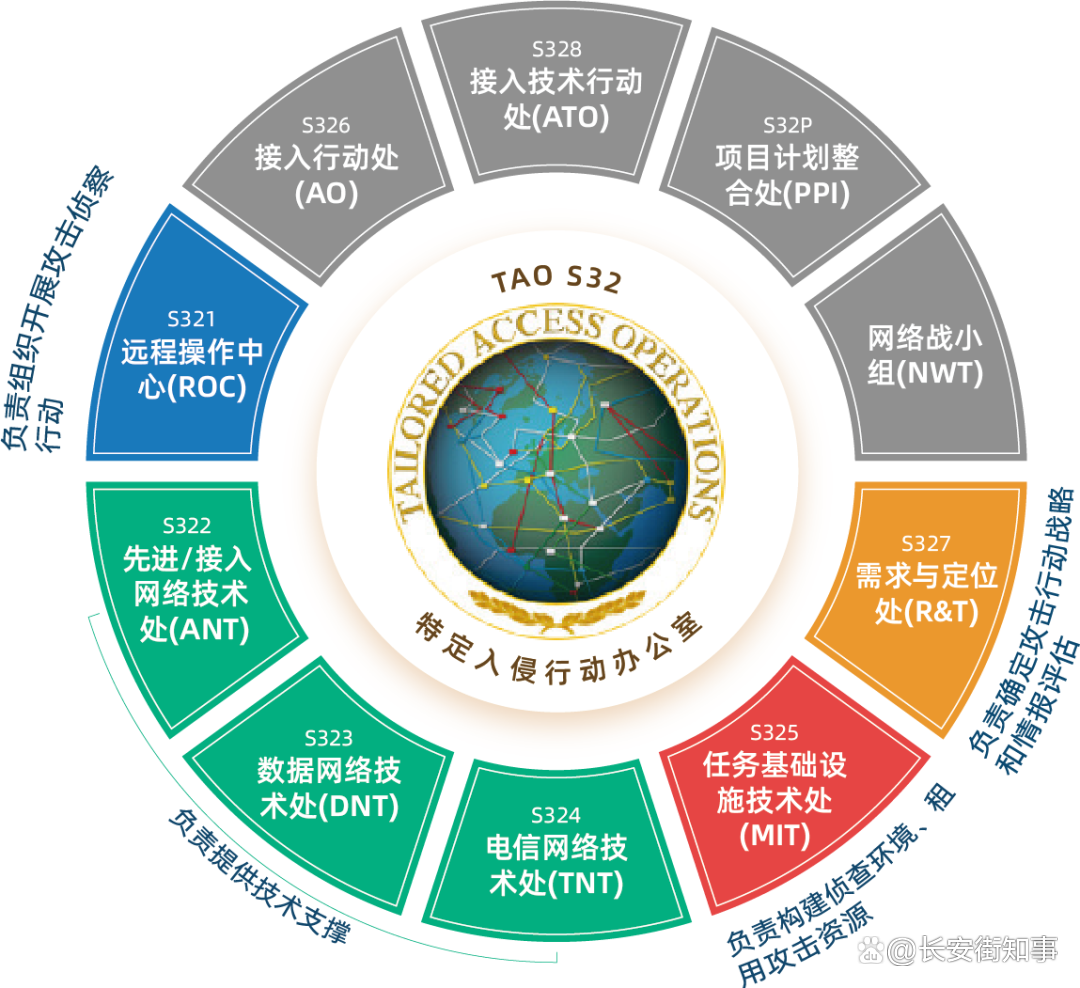
△ TAO organizational architecture and the TAO sub -department map of the "blocking XXXX" operation: CCTV News Client
The National Security Agency (NSA) has the attack on Northwestern Polytechnical University as "shotxxxx". The operation of the operation was directly commanded by the person in charge of TAO, and MIT (S325) was responsible for building a reconnaissance environment and renting attack resources; R & T (S327) was responsible for determining the attack strategy and intelligence assessment; S324) is responsible for providing technical support; ROC (S321) is responsible for organizing attack reconnaissance operations. It can be seen that the direct participation in command and action includes TAO leaders, S321 and S325 units.

△ Robert E. Joyce Source: CCTV News Client
The head of the NSA during the attack on Northwestern Polytechnical University was Robert Edward Joyce. This man was born on September 13, 1967. He studied at Hannibal High School. He graduated from Clarkson University in 1989, received a bachelor's degree, and graduated from Johns Hopkins University in 1993. He obtained a master's degree. In 1989, he joined the National Security Agency to work. He once served as the deputy director of TAO and the director of Tao from 2013 to 2017. In October 2017, he began to act as an agent of U.S. Land Safety Consultants. From April to May 2018, he served as a State Security Consultant of the White House, and returned to NSA as a senior consultant of the Cyber Security Strategic Strategy of the National Security Agency. He is currently the director of NSA network security.
- END -
"Party flags flutter at the grassroots level" Wuyuan: Quickly respond to rescue more than 70 people trapped people

Yu Yonghong, director of the town police station, tied his waist with a life rope,...
"Clean and Golden Water" specifies that small and micro power to make the village more livable
In the in -depth promotion of the construction of the Clean Clean Village, Yangjin Road Street, Jinshui District, Zhengzhou City relies on the 1+N+E smart supervision platform and the small and mi