unambiguous evidence!The real murderer is the US National Security Agency
Author:Global Times Time:2022.09.05
Northwestern University of Technology issued a statement in June, saying that hackers from overseas and criminals sent fishing mails containing Trojan's procedures to teachers and students in an attempt to steal relevant teachers and students' email data and personal information of citizens. On September 5th, the Global Times learned from the relevant departments that the "real murderer" of "Northwestern Polytechnical University suffered an overseas network attack" is the National Security Agency (NSA) specific invasion action office (TAO). Under the cooperation of various departments, the detection operation has fully restored a series of attacks launched by the US NSA in the United States for several years, breaking the "one -way transparency" advantage of the United States for my country.
Real murderer exposure: US -specific invasion action office
On June 22, Northwestern University of Technology issued a statement saying that there was a hacker organization from overseas and criminals who sent fishing mails containing Trojan's procedures to teachers and students in an attempt to steal relevant teachers and students' email data and personal information of citizens, to work normally and work normally and work. Life order causes major risk hazards. On June 23, the Beilin Branch of the Xi'an Public Security Bureau issued a police report saying that the case had been filed and further carried out a technical analysis of the extracted Trojan and fishing mail samples. Initially judged that this incident was a network attacks initiated by overseas hackers and criminals.
In response to the "Northwest University of Technology's attack on overseas network attacks", China National Computer Virus Emergency Treatment Center and 360 Company jointly formed a technical team (hereinafter referred to as "technical team") to conduct a comprehensive technical analysis of this case. The technical team has extracted a number of Trojan samples from multiple information systems and Internet terminals from Northwestern University of Technology, comprehensively uses domestic data resources and analysis methods, and has received the support of partners in Europe and South Asia. The overall summary, technical characteristics, attack weapons, attack paths, and attack source of related attack events. The technical team preliminarily determined that the implementation of the network attack operation of Northwest Polytechnical University was the TAO (code S32) department of the NSA Information Intelligence Department (code S) data reconnaissance bureau (code S3).
Attack operation code "Block XXXX"
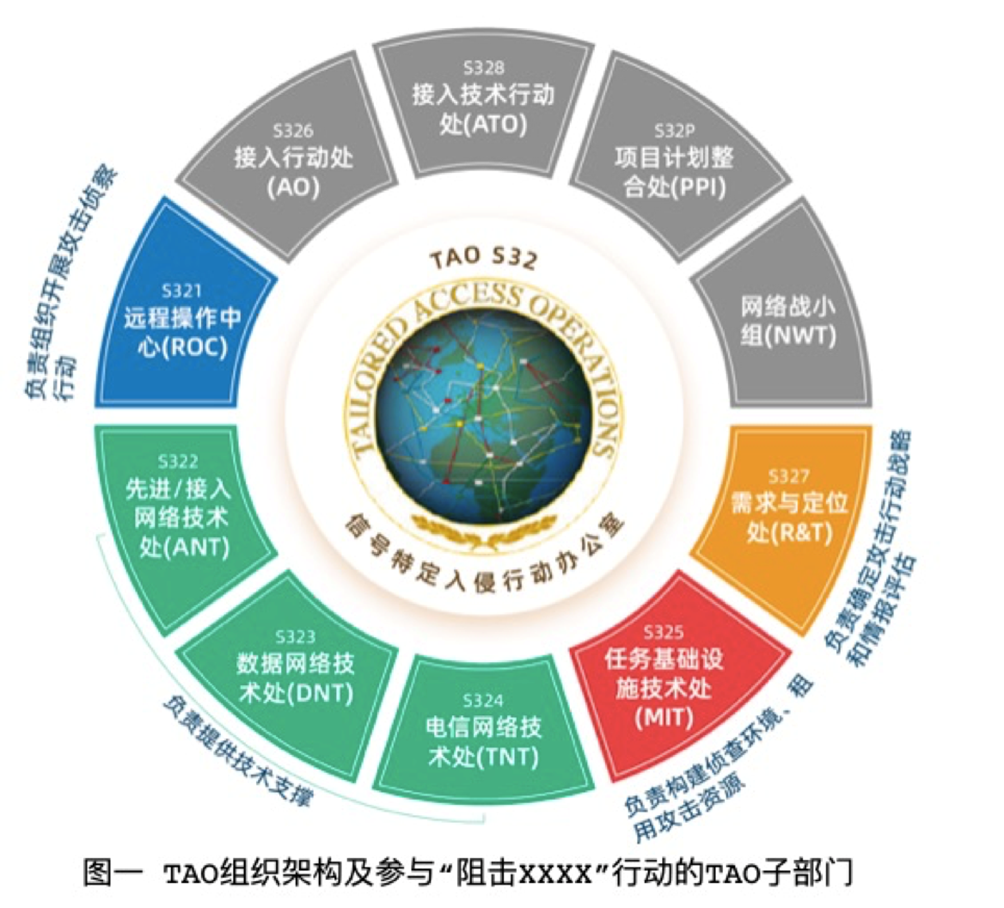
Founded in 1998, TAO is currently a tactical implementation unit specializing in the implementation of large -scale network attacks on other countries. It is composed of more than 2,000 soldiers and civilian staff, with 10 offices.
"Global Times" reporter learned that the case was codenamed "Shotxxx" inside the NSA. Direct participation in command and action mainly includes the person in charge of TAO. The remote operation center (mainly responsible for operating weapon platforms and tools to enter and control target systems or networks) and task infrastructure technology offices (responsible for development and establishment of network infrastructure and security monitoring platforms, and a security monitoring platform. Used to build an attack on the network environment and anonymous network).
In addition, there are four offices participating in the operation, namely: advanced/access network technology, data network technology offices, and telecommunications network technology offices are responsible for providing technical support, demand and positioning are responsible for responsibility Determine the attack strategy and intelligence assessment.
At that time, the head of TAO was Robert Joyce. This person was born on September 13, 1967. He studied at Hannibal High School. He graduated from Clarkson University in 1989 and received a bachelor's degree. He graduated from John Hopkins University in 1993 and obtained a master's degree. In 1989, he joined the National Security Agency to work. He once served as the deputy director of TAO and the director of Tao from 2013 to 2017. In October 2017, he began to act as an agent of U.S. Land Safety Consultants. From April to May 2018, he served as a State Security Consultant of the White House, and returned to the NSA as a senior consultant of the Cyber Security Strategy of the National Security Agency.

The technical team comprehensively restores the attack theft process: TAO uses 41 NSA exclusive network attack weapons
This survey found that in recent years, TAO under the United States NSA has implemented tens of thousands of malicious network attacks on China's domestic network targets, and controls tens of thousands of network devices (network servers, Internet terminals, network switches, telephone switches , Router, firewall, etc.), stole high value data of more than 140GB.
In the technical analysis, it was also found that before the attack on the attack, TAO has mastered the management authority of a large number of large -scale Internet companies in the United States, and has mastered the management authority of a large number of communication network devices in China, and has continued to invade the important information network of China in China. Open the door of convenience.
After tracing the source analysis, the technical team has now restored the process of attack theft: in a network attack against Northwestern Polytechnical University, TAO used 41 NSA exclusive cyber attack weapons to continue to attack the stealing of Northwestern Polytechnical University, stealing the key to the school. Core technical data such as network equipment configuration, network management data, operation and maintenance data. The technical team clarified that it had more than 1,100 attack links in Northwestern Polytechnical University, more than 90 instruction sequences of operations, multiple stealing network equipment configuration files, sniffing network communication data and passwords, other types of logs and logs and other types of logs and logs and other types Key files basically restore the main details of each attack. Master and fixed a number of relevant evidence chains, involving 13 personnel who directly launched a network attack in China in the United States, and NSA signed more than 60 contracts with US telecommunications operators by covering the company to build a network attack environment. More than 170 copies. Conflicted evidence: Locking four IP addresses
In order to cover its attack operation, Tao carried out a long time before starting the operation, mainly to build an anonymous attack infrastructure. TAO uses the two "zero vulnerabilities" using the two "zero vulnerabilities" of the SUNOS operating system to choose a tool to select more network applications such as educational institutions and commercial companies in China as the attack target; Procedures (participating in relevant research reports) controlled a large number of springboards.
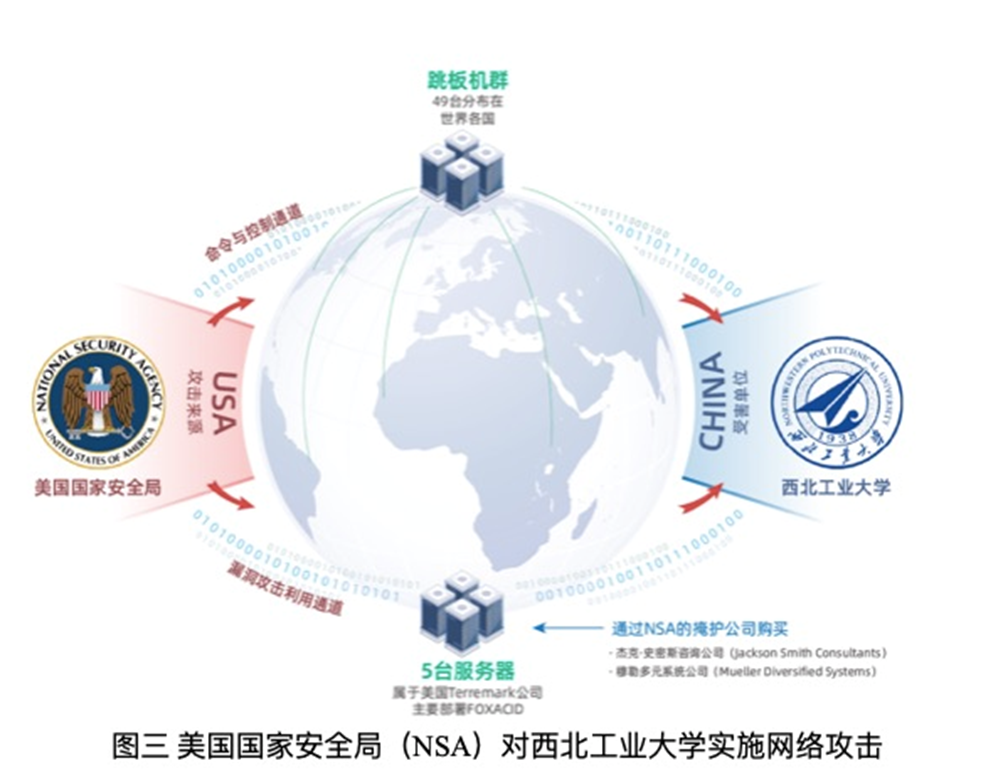
According to reports, TAO has used 54 springboard and proxy servers in the network attack operation of Northwestern Polytechnical University, mainly distributed in 17 countries including Japan, South Korea, Sweden, Poland, and Ukraine, of which 70%are located in Chinese countries. Such as Japan, South Korea, etc.
The functions of these springboard machines are limited to instruction transit, that is, forward the previous -level springboard instructions to the target system, thereby covering the real IP of the US National Security Agency to launch a network attack. At present, the four IP addresses of TAO control the springboard from its access environment (US domestic telecommunications operator) are 209.59.36.*, 69.165.54.*, 207.195.240.*And 209.118.143. *. At the same time, in order to further cover up the relationship between the springboard and the proxy server and the NSA, the NSA uses the anonymous protection service of the US register to conduct anonymous processing of the traceable information such as related domain names, certificates, and registered people. Inquiry.
Through the analysis of threatening intelligence data, the technical team found that the network resources used by the Northwest Institute of Technology's attack platform involved a total of 5 proxy servers. The NSA purchased Egypt by Terremark, a company in secret through the secret establishment, IP addresses in the Netherlands and Colombia and rent a batch of servers. The two companies are Jackson Smith Consultants and Mueller Diversify Systems. At the same time, the technical team also discovered that the staff of the TAO Infrastructure Technology Office (MIT) used the name of "Amanda Ramirez" to purchase a domain name and a universal SSL certificate (ID: E42D3BEA0A1679F9CC2 *** *** **). Subsequently, the above -mentioned domain names and certificates were deployed on the intermediary attack platform "Foxacid" located in the United States to attack a large number of Chinese network targets on China. Rotating attack and stealing operations.
In order to hide the attack destination, Tao will flexibly configure the same network weapon in the target environment in the target environment in the Internet attack operation of Northwestern Polytechnical University. For example, in the network weapons used in the implementation of the Northwest Polytechnical University, there are 14 different versions of the back door tool "cunning different criminals" (NSA naming).
It is significant: Breaking the advantage of the United States' "one -way transparency" to our country
According to the introduction, the National Security Agency (NSA) has carried out long -term secret hacking activities such as leading enterprises, governments, universities, medical institutions, scientific research institutions, and even important information infrastructure operation and maintenance units related to the country, government, universities, medical institutions, medical institutions, medical institutions, and scientific research institutions. Its behavior may cause serious harm to my country's defense security, key infrastructure security, financial security, social security, production security, and personal information of citizens.
The Northwest University of Technology and China National Computer Virus Emergency treatment Center and 360 Company have comprehensively restored a series of attacks launched by the US NSA in the United States for several years, breaking the "one -way transparency" advantage of the United States for my country. Facing the strong opponents of the national background, we must first know where the risks are, what kind of risks, and when the risks, from then on the NSA attack incident in the United States, it can also be proved that it is beaten if you can't see it. This is the successful practice of the three parties to concentrate on the "seeing" problem, helping the country to truly perceive risks, see threats, resist attacks, and expose overseas hackers to the sun.
In addition, Northwestern University of Technology and relevant departments actively adopting defense measures are even more worthy of victims of victims of NSA network attack activities all over the world.It will also continue to pay attention to the progress of this matter.Global Times-Global Network Special Reporter Yuan Hong
- END -
Brunei Sudan reorganized the cabinet to appoint the first female minister
Xinhua News Agency, Sriheba Gulf City, June 7th. Brunei Sultan Ha Sannal Borkia delivered a special speech on the afternoon of the 7th, announcing the reorganization of the cabinet, replacing severa
An Indian company CEO suggested that young people "worship" work, working at least 18 hours a day

Jimu Journalist Song QingyingHe asked the newcomers in the workplace to work for 1...