Attack penetration of my country's infrastructure!The US NSA network attacks Western Engineering University more details →
Author:China Fund News Time:2022.09.27

Source: CCTV News WeChat public account
The National Security Agency's NSA launched a network attack incident on Northwestern Polytechnical University in my country, and has made new details.
On September 27, the National Computer Virus Emergency treatment Center issued the "Report on the Investigation Report of Northwest University of Technology by the NSA Network Attack Incident (2)", which disclosed the attack and penetration of the Specific Invasion Action Office (TAO) under the National Security Agency (NSA) The process of the Northwestern University of Technology, the stealing sensitive information of Northwestern Polytechnical University and Chinese operators, and announced the IP list of the weapon platform used by TAO network attacks on Northwestern Polytechnical University and the springboard IP list used.
On June 22 this year, Northwestern University of Technology issued a "Public Statement" stating that the school was attacked by overseas networks, and the Xi'an police officially filed a case for investigation. The technical analysis of the case, and released the first "Northwest Institute of Technology to suffer the NSA network attack survey report" on September 5th. Action Office (TAO). Details &&&
Single point breakthrough, gradual penetration, long -term stealing
TAO stealing key sensitive data of Western Engineering University
The second survey report released today shows that the National Security Agency (NSA )'s specific invasion action office (TAO) has a strong network attack technology tactics initiated by other countries. , Long -term stealing.
360 Company Network Security Expert Bian Liang: It can batch deviations and viruses on the equipment in the network or a section of IP to obtain relevant permissions, which can be automated. It needs to be lurking and long -term control in the future, and it needs to be targeted to steal relevant documents, and it needs to be destroyed when retreating. Someone needs to be operated behind this. The whole process is semi -automated.
The technical team found that after a long time of careful preparation, the "Sour Fox" platform shall be used to carry out intermediate hijacking attacks on the internal hosts and servers of Northwestern Polytechnical University. , Further deployment of stealing secret weapons.
TAO uses the stealing account password
Infiltration and controlling China Infrastructure Core Equipment
The report shows that by stealing key sensitive data such as account passwords, operating records, and system logs such as the operation and maintenance and technical personnel of Northwestern Polytechnical University operation and maintenance and technical personnel. Permanent, router and other device configuration information, FTP server document information information.
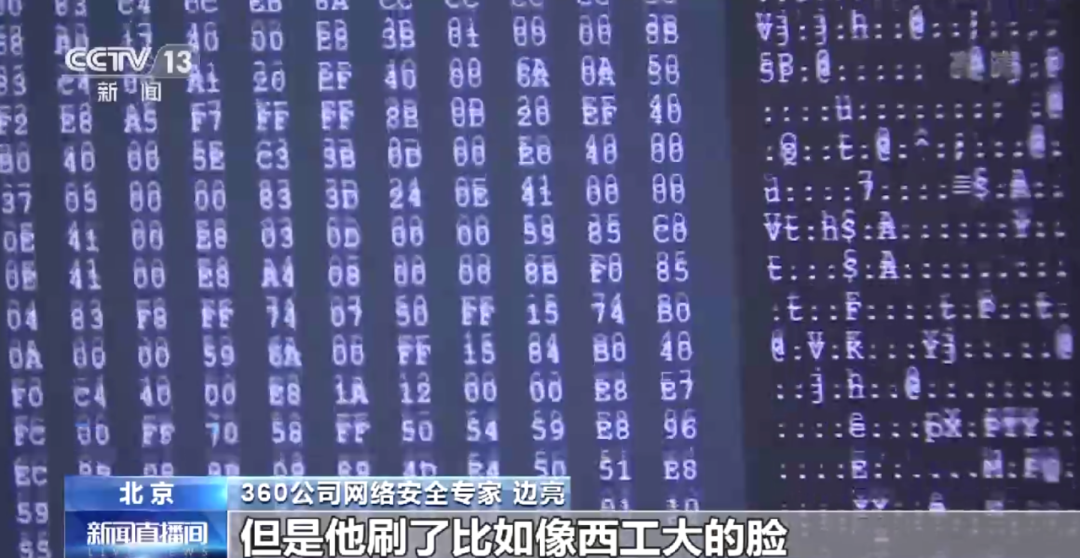
360 company network security expert Bian Liang: After controlling the related equipment of Western Industry University, use Western Technology University to attack other units. This process is the "legal" of quotation marks. It is equivalent to a protective mechanism similar to face recognition in our database. For example, if an American comes, he can stop it directly, but he brushed the face of Western Engineering, and we will think that he is a normal user and let him go. But in fact, the relevant server of Western University of Technology was controlled by TAO, and TAO further launched an attack on other units.
Based on the characteristics of the specific invasion operation office (TAO) attack link, penetration method, Trojan sample and other characteristics, they have found that their illegal attacks infiltrate infrastructure operators in China have built remote access to the core data network of infrastructure operators ( The so -called) "legal" channel realizes the infrastructure control of China's infrastructure.
Stealing the privacy data of sensitive status in China
The report shows that the Cisco PIX firewall, Tianrong Criminal Firewall and other devices of the Specific Invasion Action Office (TAO) enters the operator network as a "legally" "legal" identity as a "so -called)"Expansion and expansion, control the service quality monitoring system and SMS gateway server of related operators, use the "magic school" and other weapon tools specifically for operators' equipment to check a group of sensitive status in China, and pack user information and encrypted after encrypted user informationBack to the headquarters of the National Security Agency by multi -level springboard.
- END -
For the first time, scientists have discovered a tentacle -like creature in the Pacific Ocean, or new species of marine basins

Science Fiction Network July 18 (Wang Ziyu) Recently, according to CNET, scientist...
The construction of Zhongguancun Science City runs out of "acceleration"

Xinggu Industrial Park/PictureIn order to go all out to promote the re -production...