Your personal information is leaked like this
Author:Jiangsu Police Time:2022.09.18


Your personal information
It was leaked like this
Notice!
Speaking of privacy leakage
Some people will say

But look at your phone
SMS, harassment calls, spam,
Can you still take a chest and pack your chest?

So,
Which behaviors are leaking your privacy?
01
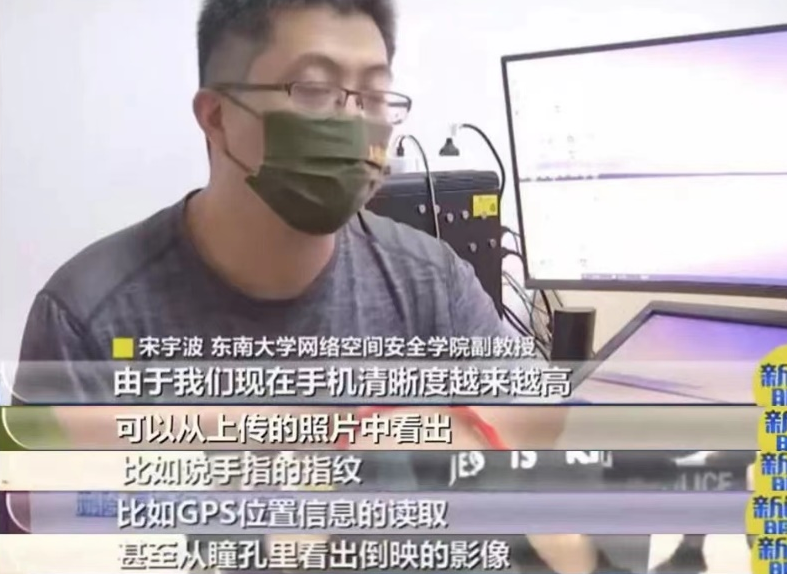
Original mobile phone
Everyone will choose to upload the original picture when you are exposed to the picture
Usually when you take pictures on your mobile phone
Mobile phone will generate photos related parameters synchronously
There are many sensitive information in it
mainly include:
Shooting time, equipment used,
Shooting parameters, image processing parameters,
GDS positioning data, etc.
And upload the original picture
All of these will be uploaded
02
Mobile phone input method
Sometimes you will find out what you just talked with friends
It will soon appear in the shopping recommendation table
This is actually a ghost in the input method!
When some input methods are installed
Will clamp the prompts in the privacy clause
Most people may not look at it carefully

Some input methods are more direct
A pop -up window horizontally there
Do you disagree? The ____ does not work!
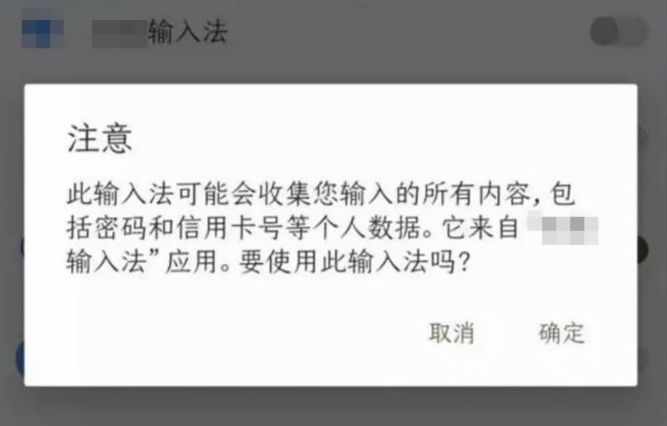
that's it
No matter what you say
All of your information are recorded!
03
Mobile phone clipboard
The clipboard is like a courier transit station
Every time you copy the information, you will get here first
Only then will be sent to a new address

In this process
The clipboard is exposed to some of your privacy information
There is often no way to avoid

If it is not cleaned up
When you open other applications
Those applications will peek at your privacy

04
Mobile phone Bluetooth
Is the mobile phone Bluetooth always open?
see this

That is
As long as others and your Bluetooth are on the same network
And your Bluetooth is opened
Not only can he steal your sensitive information
You can also track you

05
Netdisk link leakage
I don't know when you share the network disk
Will there be a password
If not
This link is open
It will be displayed on your app personal homepage
See directly by others
The biggest risk is from the Internet crawler
Many criminal gangs
Use crawlers to capture personal information to make money

There are many online disk search websites
Is crawler technology
Search through keywords
You can find the content of someone else's network disk
I will take a while
You listen to it
1
Fill in personal information carefully online shopping
When applying for shop members and filling in the receipt information, if the necessary real -name system, you can choose a nickname instead. If you choose the courier station, express cabinet, etc., you don't need to accurately reach the specific house number of the address. If a merchant calls for praise, it can be complained on the relevant platform.
2
Be careful when handling personal information
The content of the personal information must be exited, deleted or destroyed in time. For example, the application software on the public computer must be exited in time, and the files should be deleted in time; Paste the courier form to destroy.
3
Carefully authorize when using mobile phone software
When authorized APP -related permissions, you must carefully check the contents of the notification, and you need to turn off for the use of the software. At the same time, account authorization must also be canceled for long -term unused third -party platforms or websites.
4
Pay more attention when using personal information
After using the relevant documents, you should delete the photos in the mobile phone in time, and don't keep it all the time. At the same time, after a copy of the relevant documents, it is best to write in the blank space that "this copy is only for XX use, he uses invalid" to ensure that personal information is not used by others as much as possible.
5
Do not care about publishing information on the open platform
Before publishing the content on the open platform, you must check whether your personal information is exposed. For example, when you are married, you must cover up key content such as your personal name, ID number, etc. At the same time, when interacting with netizens on the platform, do not easily leave personal contact information, family address, etc. When participating in the questionnaire survey of the open platform, do not fill in related content and other related content.
6
Pay attention to taboos when you are exposed to your circle of friends
1. Do not take train tickets, airplane tickets, boarding pass
2. Do not take passports, door keys, license plates
3. Don’t take the position
4. Don't take photos and names of children
5. Don't take photos of the elderly at home
The last point! Intersection
Please see, please,
Please master the mobile phone use tips.
Police tip
1. "People nearby" please close
The function of "nearby people" on WeChat can locate your position. You can click "Settings-General-Discover Page Management-People Nearby" to select "Close the Import of the Discover Page".
2. "Allow search", please close
In WeChat "Privacy", close "Search for Me" and "You Can Search for me via a mobile phone number".
3. "Allow View" please turn off
Turn off "Allow strangers to view ten friends circle" in the WeChat "Privacy" option.
4. Don't panic when you lose your mobile phone
Call the operator (China Telecom 10000, China Mobile 10086, China Unicom 10010) to lose mobile phone number; call the bank to freeze mobile online banking; relieve the Alipay 95188; relieve WeChat 110.qq.com.
These tips to protect personal information
Have you mastered it?
Hurry forward to your dearest person
Planning | Sun Ye Dai Xiaogang Zhang Azheng
- END -
This year's netizens have split the most lies: I have read the agreement

Editor's Guide: The most lied in this life, that is, obviously did not read the no...
PingPong partner Luo Yonglong: Cross -border e -commerce cannot be separated from the digitalization of industrial chains and other industrial chains

Economic Observation Network reporter Tian Jin Cross -border e -commerce has becom...