The Northwest Engineering University was attacked by the US Open, and another detail was exposed!
Author:Banyue talk about new media Time:2022.09.13
"Global Times" reporter learned from the relevant departments on the 13th that
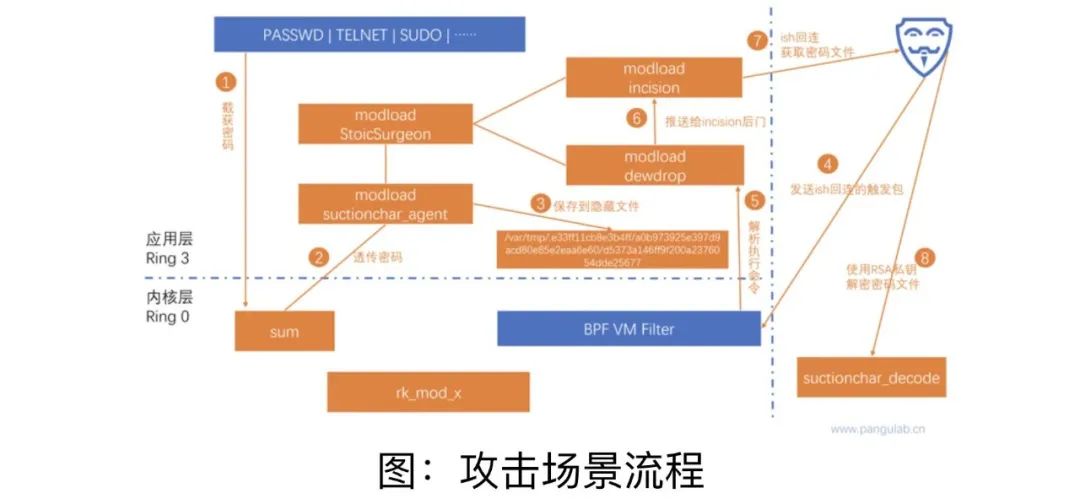
In Northwestern University of Technology, the National Security Agency (NSA) network attack incident, the sniffing secret network weapon named "tea drinking" is one of the most direct "culprits" that lead to a large amount of sensitive data.
In this regard, network security experts suggested that in the process of informatization, it is recommended to choose domestic products and "zero trust" security solutions.

National Security Agency (NSA) Headquarters, Mideburg, Maryland
On September 5, relevant Chinese departments announced to the outside world,
Northwestern University of Technology had previously stated that it was attacked by an overseas network. The attacker was the National Security Agency (NSA) specific invasion action office (TAO).
Since then, the National Computer Virus Emergency Treatment Center and Beijing Qianpan Ancient Laboratory have further analyzed the invasion. In the latest survey report, the technical details of the US's attack on attack have been made public:
That is, the sniffing secret network weapon named "Tea Drinking" in the 41 network weapons is one of the most direct "culprits" that lead to a large number of sensitive data theft.
Related network security experts introduce,
TAO uses "tea drinking" as a tool for sniffing theft, implanted it into the internal network server of Northwestern University of Technology, stealing the login password of remote management and remote file transmission services such as SSH, so as to obtain access permissions of other servers in the internal network and realize The inner network moves horizontally and sends other high -value servers to other sniffing secrets, persistent control and concealed disappearance network weapons, causing large -scale, persistent sensitive data theft.
Technical analysis and research judgment,
"Tea drinking" can not only steal the account passwords of multiple remote management and remote file transmission services on the server, but also have strong concealment and environmental adaptability. The network security experts in the above said that after the "tea drinking" is implanted into the target server and network equipment, it will disguise itself into a normal background service process, and use a modular method to send malicious loads in stages. Hiddenness, it is difficult to find. "Tea Drinking" can be operated hidden on the server, monitor the user's input on the terminal program of the operating system console in real time, and intercepts various user names and passwords, like the "voyer" standing behind the user.
Cyber security experts introduced: "Once these username passwords are obtained by TAO, they can be used to attack the next stage. Even if these usernames password access to other servers and network devices, they will steal files on the server or send other delivery of other. Network weapon. "
Technical analysis shows,
"Tea drinking" can be effectively integrated and connected with other NSA network weapons to achieve "seamless docking". In February of this year, the Beijing Qi'an Pan Ancient Laboratory publicly disclosed the technical analysis of the top weapon "Electric Screen Operation" (BVP47), which is affiliated to the National Security Agency (NSA) hacker organization- Anpan ancient named "Electric Screen Action" attack activity. In TAO's incident of cyber attacks on Northwestern Polytechnical University, the "Tea Drinking" sniffing theft tools and BVP47 Trojan Programs were cooperated with other components to implement joint attacks.
According to the introduction, the BVP47 Trojan has extremely high technical complexity, architecture flexibility, and ultra -high -intensity analysis and evidence collection and confrontation characteristics. It is used to peep and control the information network of the victims with the "tea drinking" component, secretly stealing important data. Among them, "Tea Drinking" sniff the hippocampus secretly lurking in the information system of the victims, and is responsible for listening, recording, and returning the "results of the war" -the account number and password used by the victims, whether it is in the inner network or the external network Essence
The report also pointed out,
With the gradual deepening of the survey, the technical team also discovered the "tea drinking" attack traces in other institutions outside Northwestern Polytechnical University. It is likely that TAO uses "tea drinking" to launch large -scale network attacks to China.
It is worth noting,
During the multiple cyber attacks implemented by the United States to other countries, the US IT industry giants have repeatedly appeared. For example, in the "Prism" plan, the US love department has the authority of senior administrators and can enter the servers of Microsoft, Yahoo, Google, Apple and other companies at any time, and the long -term secrets are tailored. In the hacking tools used by the "Formula" organization announced by the "Shadow Broker", Microsoft, Cisco, and even some Chinese Internet service providers' "zero vulnerabilities" (0Day) or back doors appeared.
"The United States is using its technical dominance in the field of software and hardware in the network information system. With the comprehensive cooperation of the US IT industry giant, using a variety of cutting -edge network weapons to launch non -different network attacks worldwide in global The account password is prepared to log in to the victim's information system at any time to implement a larger scale stealing or even damaging activities. Its network hegemony is undoubtedly revealed. "
Therefore, network security experts suggest that users reinforce key servers, especially network operation and maintenance servers, regularly change the administrator passwords of the server and network devices, and strengthen the audit of the network network traffic, and timely find abnormal remote access requests. At the same time, in the process of informatization, it is recommended to use domestic products and "zero trust" security solutions. ("Zero trust" is a new generation of network security protection concepts. No one, equipment, and systems inside and outside the network default.)
This expert further pointed out,
Whether it is data stealing or system destruction and paralysis, network attacks will cause huge damage to network space or even the real world, especially for attack behavior for important key information infrastructure, "network space is largely mapping of physical space, and network activities are easy to easily. The characteristics of crossing the border make it a pioneer of continuous struggle. Without network security, there is no national security. Only by developing our asymmetric competition in the field of science and technology can we establish a China, independent network protection and confrontation capabilities. "
Source: Global Times-Global Network (Special Reporter: Yuan Hong)
Responsible editor: Guo Yanhui
School pair: Qin Daixin Meng Yahe (intern)
- END -
China Telecom's net profit in the first half of the year will increase by 3.1% year -on -year in the second half of the year will increase the investment ratio of the digital economy sector
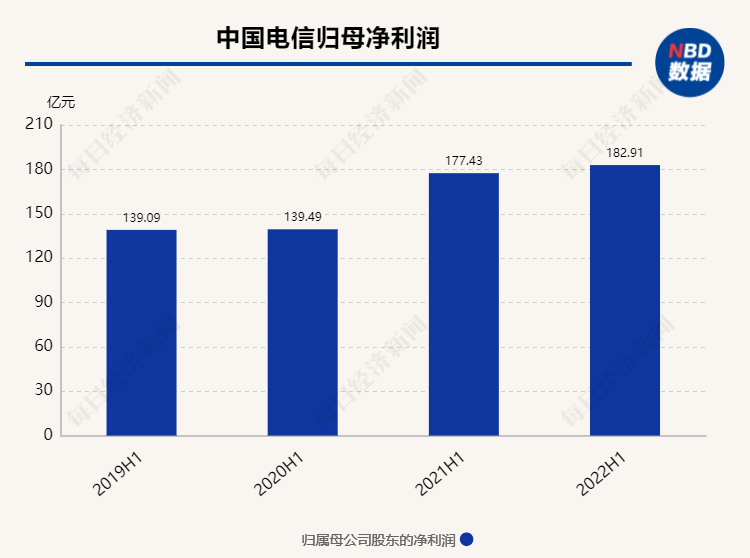
On the evening of August 16, China Telecom (SH601728, stock price 3.75 yuan, marke...
The "Tianhe" of the National Defense University of Defense won the first world first
Hunan Daily, June 24 (All Media Reporter Shi Quanjiang Gao Lihua) Recently, the reporter learned from the School of Computer Science and Technology of the University of Defense Science and Technology