Cyber security participation!Do you know these knowledge?
Author:Beijing Forestry University Time:2022.09.07

Without network security, there is no national security
There is no economic and social stability operation
The interests of the people and the masses are also difficult to guarantee
September 5th to 11th
It is 2022 National Network Security Propaganda Week
The theme of this year is
"Cyber security depends on the people's network security"

In social life
Ratch virus, telecommunications fraud, public places
WiFi trap, invincible personal information leakage
Once the harm occasionally occurs
Beijing Forestry University
Joint Information Construction and Management Office
Copy typical scenes
Teach you how to deal with common network security risks
Come and learn with the officials!
Pretend to be a hot spot
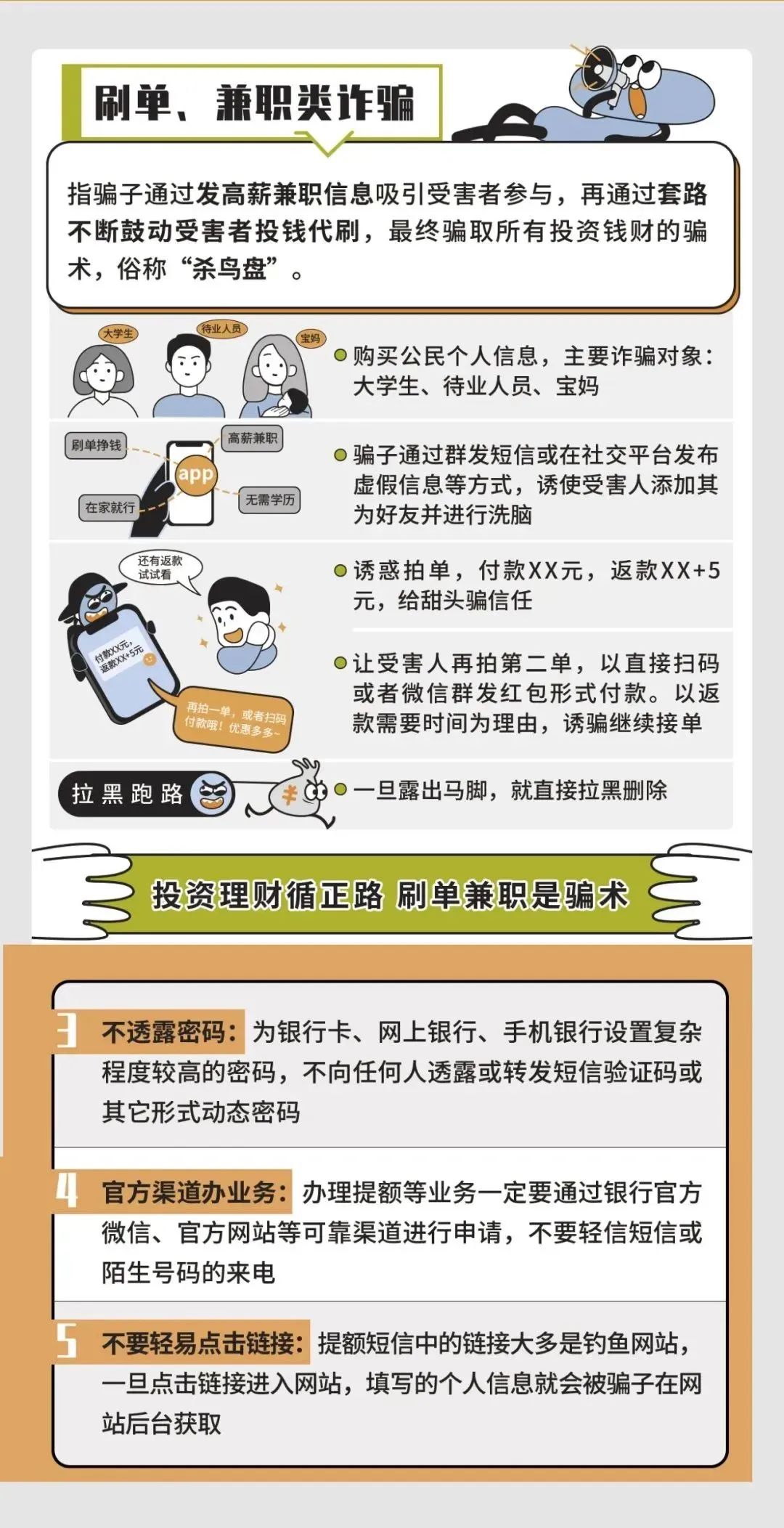
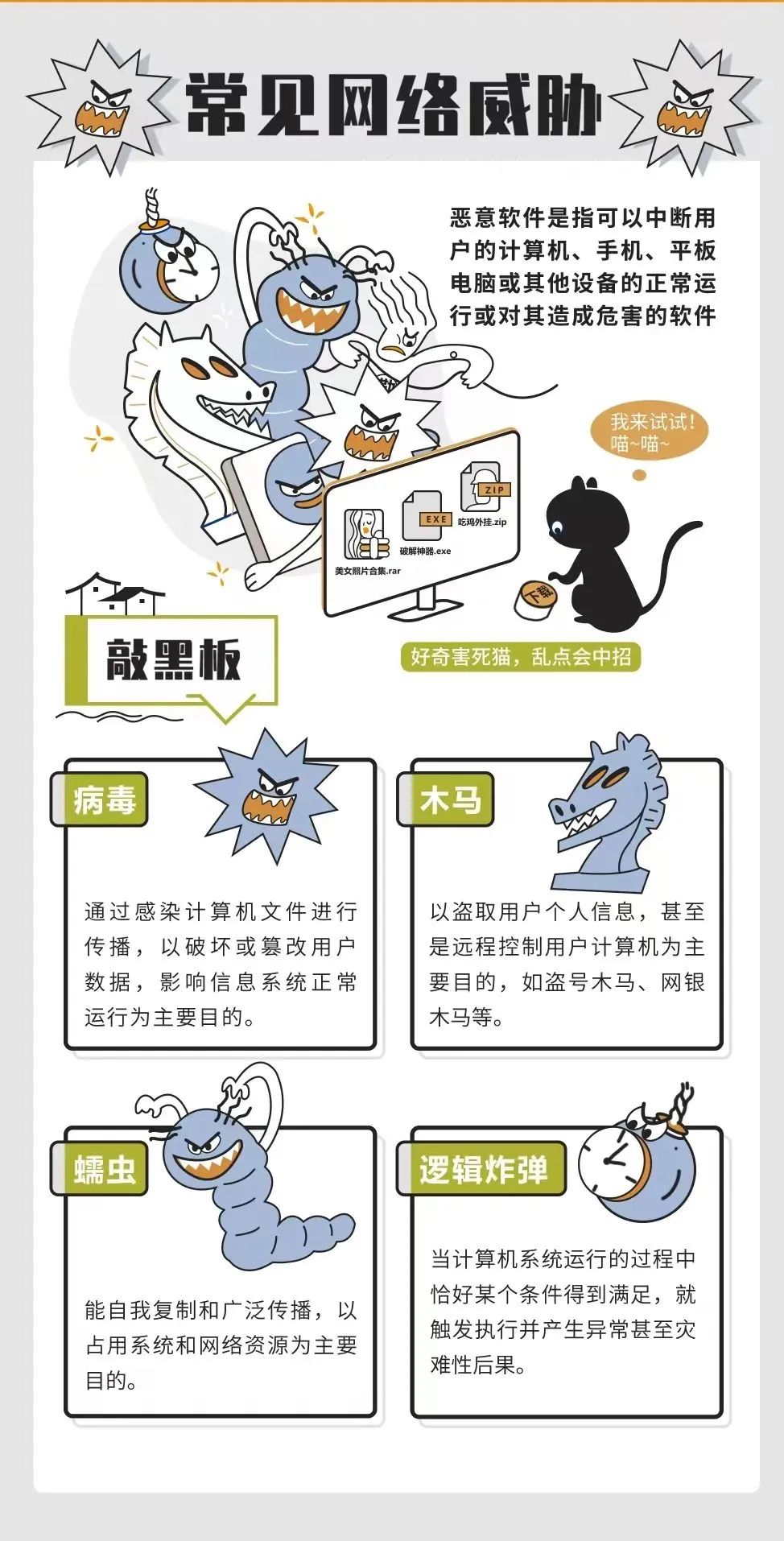
The mobile phone is a bit expensive, and the network can save traffic fees. At present, home wireless broadband routers are very popular. Due to the limitations of wireless signal transmission, commercial institutions usually use multiple access points to provide regional signal coverage. The criminals are set up by setting up counterfeit/high imitation/cottage Wi-Fi, and attract users to connect with similar names. All your upload download content is mastered by hackers!

Precautions
1. Careful and careful false: Wi-Fi provider to confirm the hotspot name and password to the Wi-Fi provider in public; Wi-Fi risk that can be accessed without passwords is high, try not to use it.
2. Avoid sensitive business: Do not use public Wi-Fi for shopping, online bank transfer and other operations to avoid logging in to account and input personal sensitive information. If the safety is required, you can use VPN service if you have conditions.
3. Close Wi-Fi automatic connection: Hackers will establish fake hotspots of the same name, and use the advantages of close signal to become the "evil twins" directly entering the point. Once the phone is connected automatically, it will cause information leakage.
4. Pay attention to security reinforcement: Set up strong passwords for Wi-Fi router and opening WPA2 is the most effective Wi-Fi security setting.
5. Run completely scanning: Install security software, carry out security scanning such as Wi-Fi environment to reduce security threats.
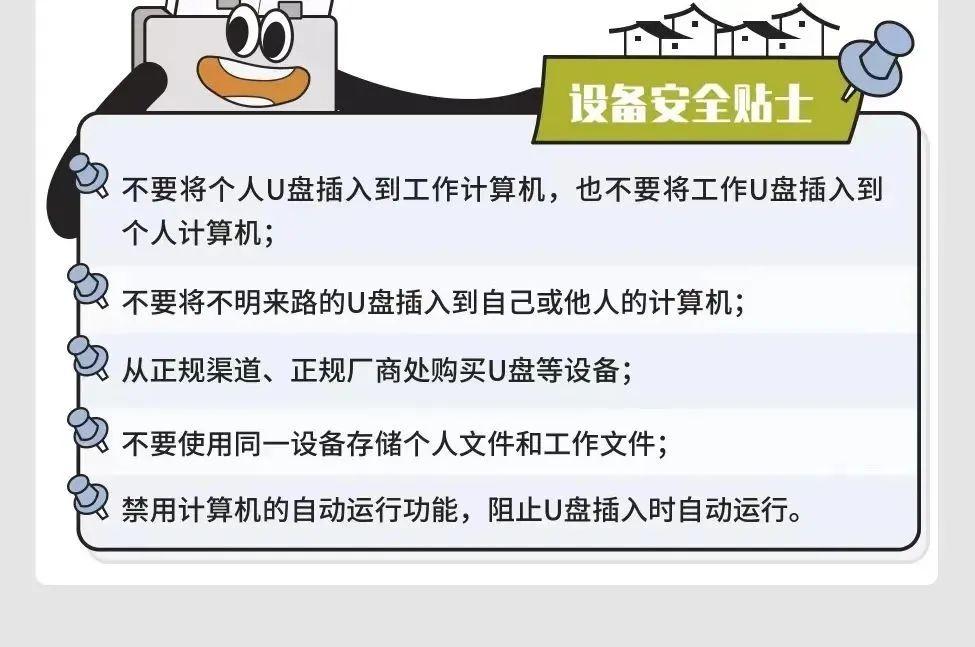
Personal information protection
Once personal information is leaked, illegally provided or abused, it may endanger the safety of people and property, which can easily lead to personal reputation, physical and mental health damage or discrimination treatment.

Precautions
1. Tear the courier list completely.
2. Refuse to participate in constellation and personality test.
3. Share the delivery flow confirmation is an official product or business activity, otherwise it is suspected of inducing sharing.
4. Everyone who requires input personal information is fake red envelopes.
5. Try not to expose the picture on the way to the trip.
6. Turn off the GPS when taking pictures, delete the location related information in the picture attribute, and send a screenshot of the photo.
7. The circle of friends sets access rules to limit the scope of access.
8. Pay attention to information leakage, timely adjust setting passwords, replace credit cards, etc.
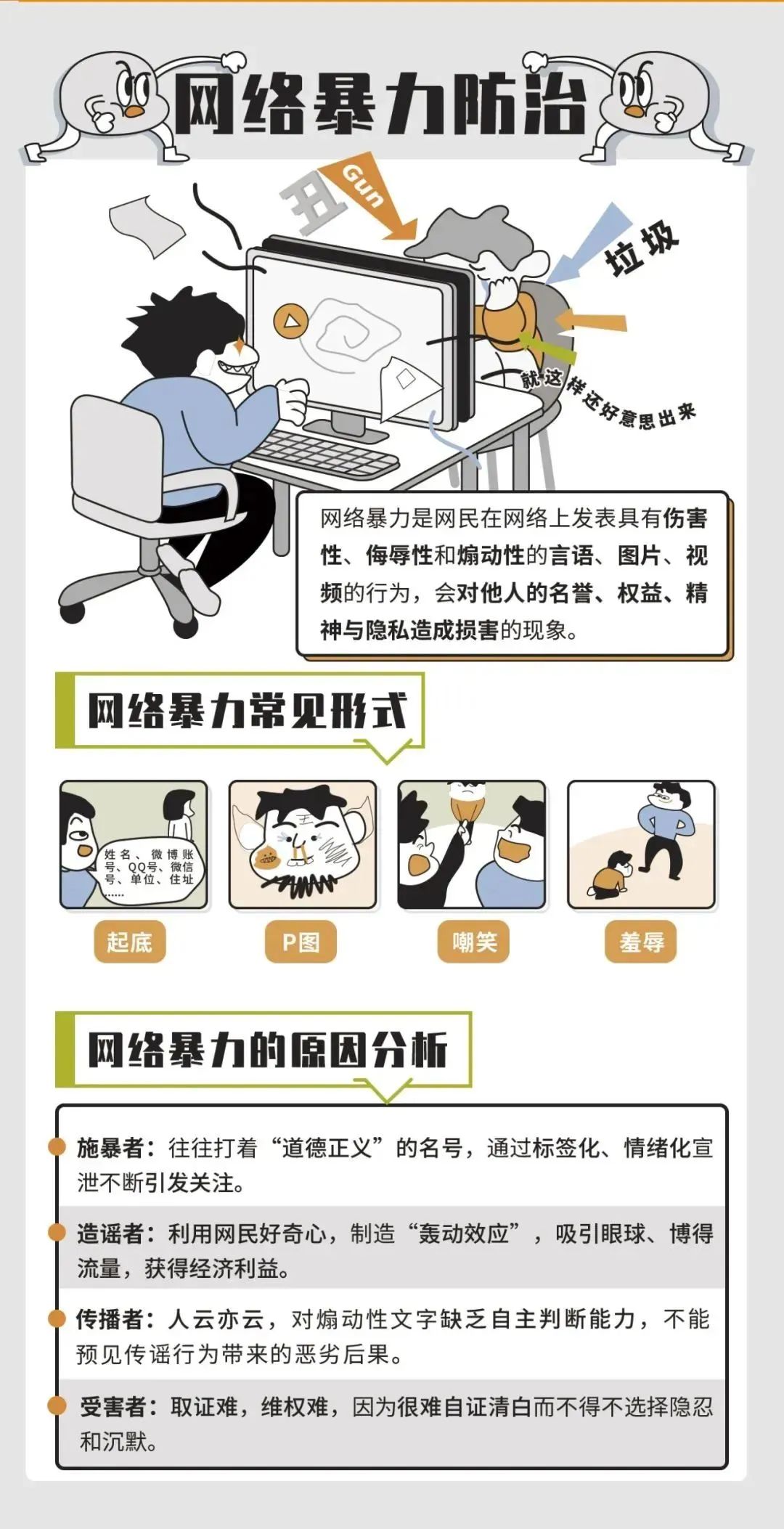
Malicious QR code
The QR code is used on the plane to use several and binary numbers 0 or 1 relative graphics to represent the geometric form of data information. The three squares on the corner are used for the two -dimensional code scanning equipment for positioning. A large amount of activities such as information acquisition, advertising push, preferential promotion, anti -counterfeiting, payment and other activities.
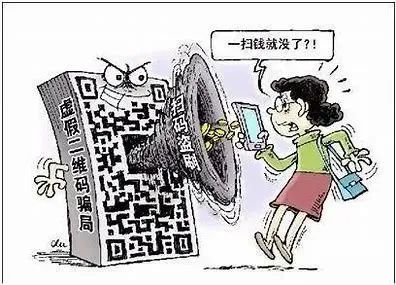
Precautions
1. Pay attention to the source: to be vigilant for various QR codes on the street, do not scan the QR code of unknown sources, such as the payment code on the fake parking ticket.
2. Safety scanning: Use the QR code security detection software such as mobile phone housekeepers to assist in determining whether it is a malicious website and whether there are malicious software behind it.
3. Differential true and false: Some scammers unlock the QR code on the shared bicycle covering a new, transparent QR code, or printing paper on the car. When requesting or downloading software, pay attention to discern's whereabouts and software sources.
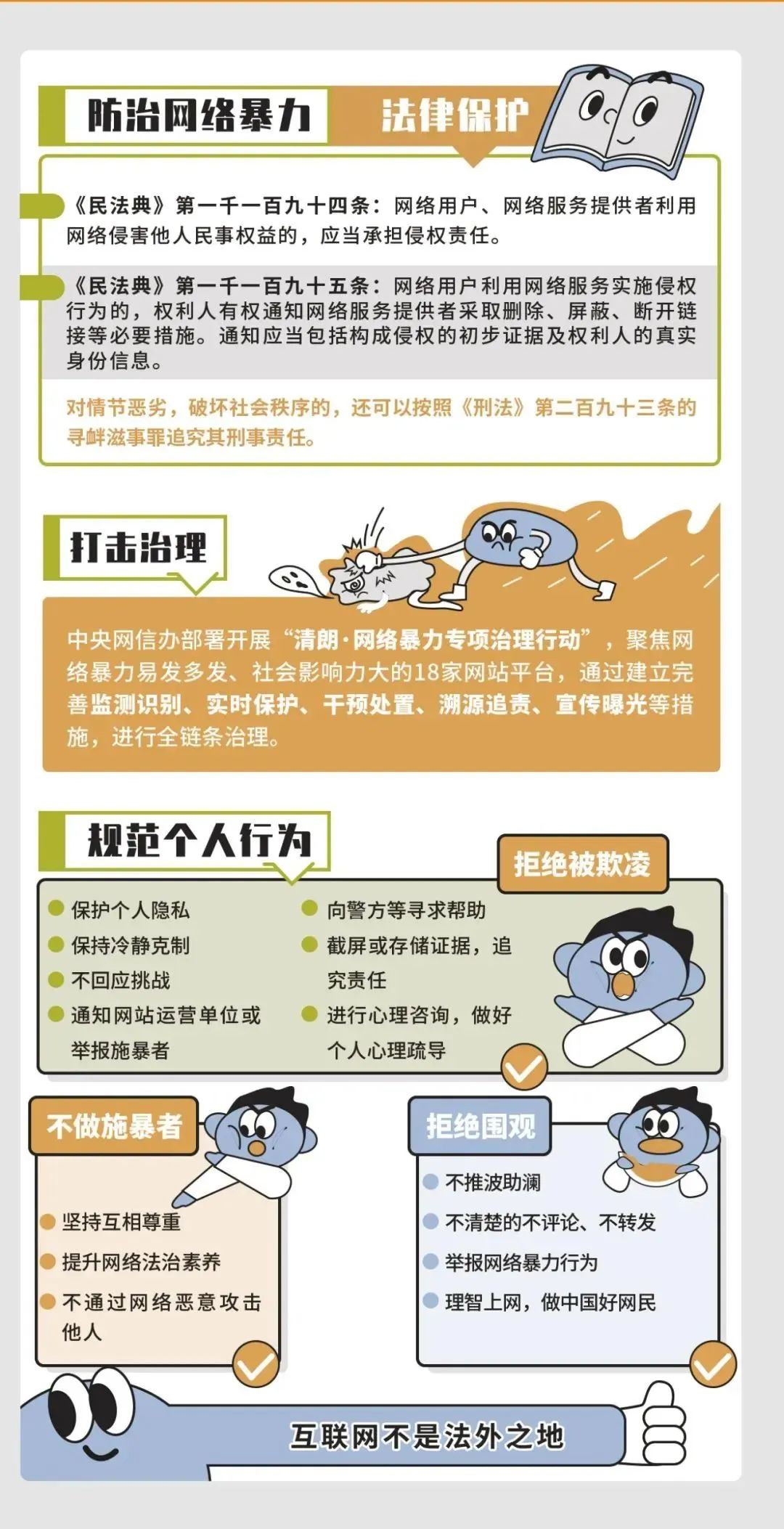
Password safety
The password is commonly known as a password, which is a string of characters that have proved their identity to computers/websites, such as 123456, 1Q2W3E, PO $ $ W0rd, etc.

Precautions
1. Avoid weak passwords
(1) Do not include the username;
(2) Try not to use words in the dictionary;
(3) Do not reuse the password that I used to use;
(4) Do not use adjacent keys on the keyboard, such as QWERTY, 123456,! @#¥%
(5) Do not use personal information, such as driver's license, telephone, etc.;
(6) Do not use the sixth and eighth positions of the ID card, and do not use common prefixes such as BJFU BJFU.
2. Set strong password
(1) At least 8 characters;
(2) Including at least uppercase and lowercase letters;
(3) Contains at least one number;
(4) Contains at least one special character;
(5) Different websites set different user names and passwords;
(6) Use software such as Keepass to help manage passwords.
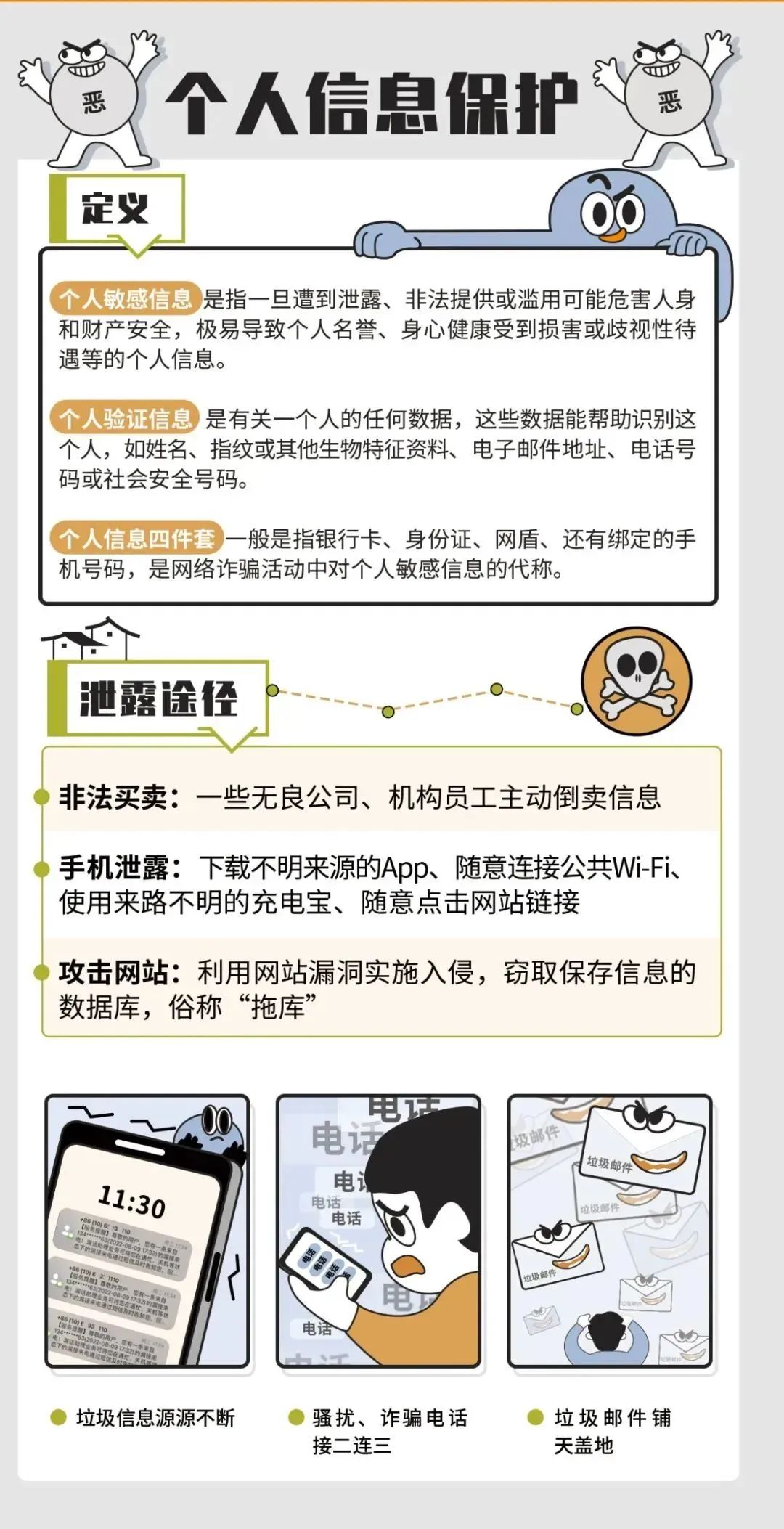
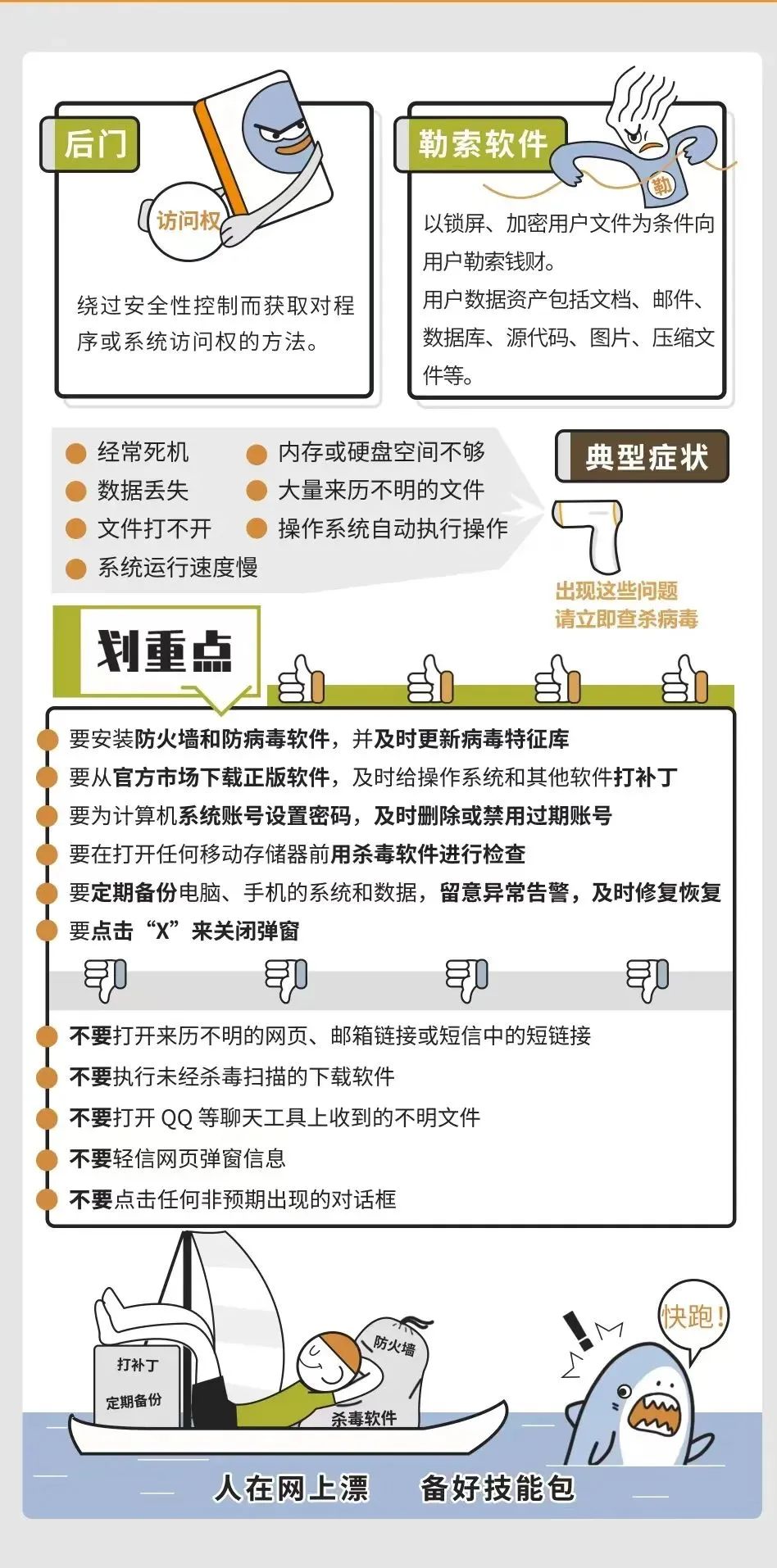
Ransomware
The ransomware is a type of malware to lock the system screen or lock the user file to prevent or restrict the normal use of the user's normal use of the computer, and in order to settle the user to pay the ransom. The scary strategies of ransomware include: lock the screen, delete backup files, accelerate deletion files, increase the amount of ransom. The form of ransom includes: real currency, Bitcoin and other virtual currencies.

Precautions
1. Refusable ransom: Paying ransom will promote the attacker's anger. The attacker will also analyze user finance and data value through the ransom speed of user payment, and may be stared at.
2. Anti -virus and anti -virus: try to download software from the official website, install regular anti -virus software, and perform virus scanning before running download software. 3. Update in time: Pay attention to the security announcement of the operating system, install the security patches in time, and block the vulnerability as soon as possible.
4. Clocking port: Close the useless computer service/port, turn on the Windows firewall to reduce the "channel" of being attacked.
5. Backup: Use the disc/mobile hard disk and other media to regularly backup the documents, emails, databases, source code, pictures, compression files and other types of data assets and save them.
The above is about
How to cope with common network risks
Everyone must remember!
At the beginning of school, to effectively improve our school's 2022 freshman
Awareness of anti -fraud and safety awareness solidly promotes campus anti -fraud and anti -fraud work
Our school invites the Haidian Branch of the Beijing Public Security Bureau
Anti -Telecom Network Fraud Center Police Officer Zou Hong
It is 6321 new students
Carry out live broadcast lessons for anti -fraud and security education
Pass the webcast class
Beijing Forestry University official WeChat and WeChat video number broadcast
More than 14,000 people watch online
Improving the safety awareness of teachers and students
Further build the campus anti -fraud defense line
Police Officer Zou Hong was deceived by the teachers and students of colleges and universities, using pictures, videos, call recording with the victims, and other materials. The basic characteristics and fraud routines of logistics customer service category and other high -incidence fraud have proposed targeted precautionary suggestions to introduce and mobilize new students to download and use the "National Anti -Fraud" APP.

It is reported that our school attaches great importance to campus prevention and anti -fraud publicity and education, and has carried out activities such as anti -telecommunications fraud publicity and education into dormitory, theme class meeting, and signing a warning committee for preventing telecommunications fraud warning. Next, the school will continue to increase publicity, create a good anti -fraud campus atmosphere, and better protect the safety of teachers and students and employees.
Cyber security has nothing to do with
Please continue to follow
2022 National Network Security Propaganda Week Activity
What is National Network Security Propaganda Week
"National Network Security Propaganda Week", "China National Network Security Propaganda Week", is a theme activity carried out to "build network security and share network civilization". Cyber security issues, for the hot issues of public concern, organize a series of theme publicity activities such as network security experience exhibitions to create a good atmosphere of everyone's responsibility and participation of everyone.
The 2022 National Cyber Security Publicity Week will be held nationwide from September 5th to 11th. The theme of the event is "network security is the people, and network security depends on the people." In the meantime, through online and offline exhibitions and interactions, it will carry out activities such as cybersecurity education cloud classrooms, network security events, cybersecurity competitions, network security entry into the grassroots level, and 6 major series of theme days such as campus day, telecommunications day, and personal information protection day.
Cyber Security Knowledge Breakfast Manual
In 2022 National Network Security Propaganda Week activities

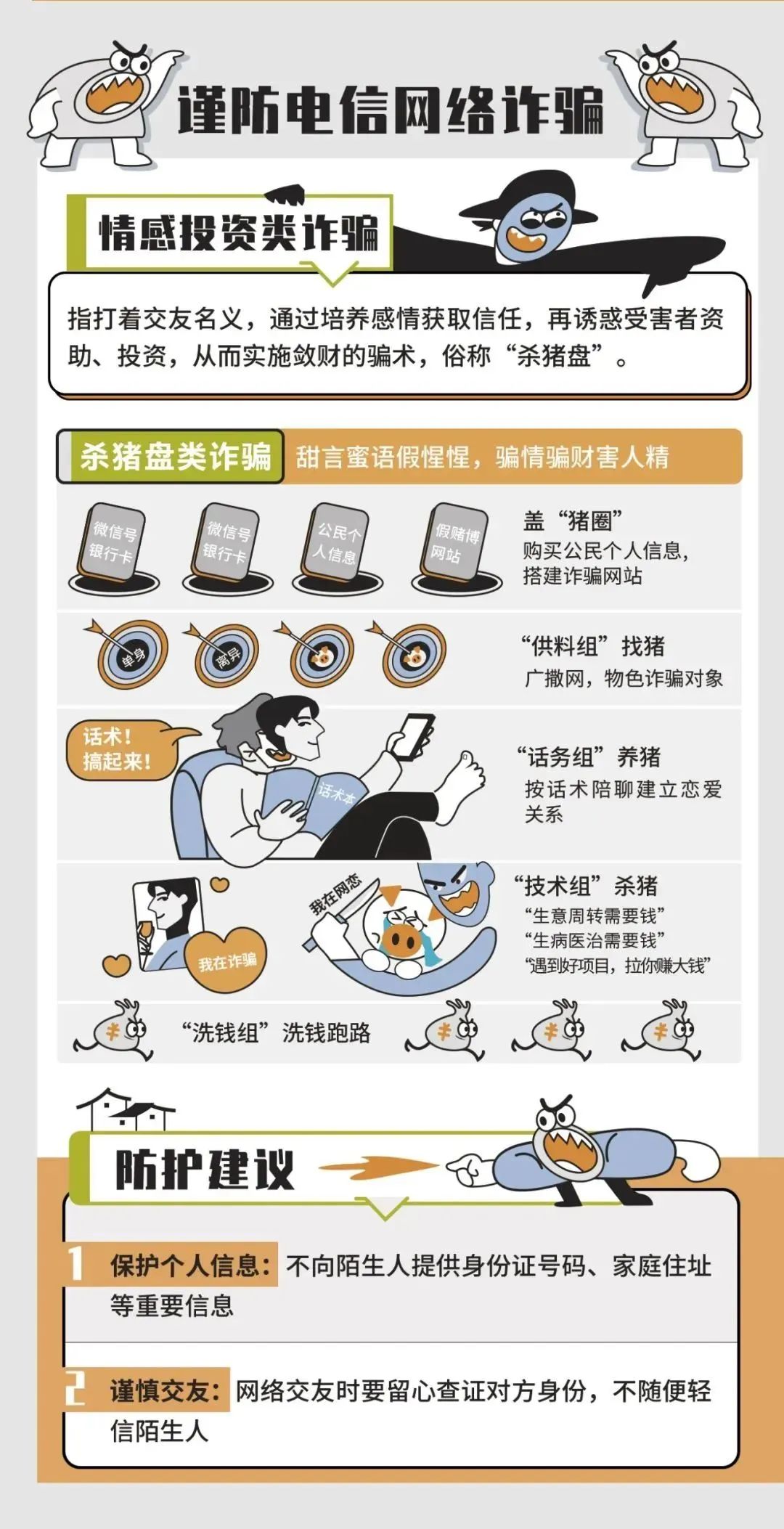

Our school adopts online activities
Organize the participation of "college teachers and students with the above network security class"
Participate in the national college student network security knowledge answer questions
Publicity network security knowledge
Improve the awareness of students' network security precautions
Course Introduction
The Ideological and Political Work Department of the Ministry of Education and the Criminal Investigation Bureau of the Ministry of Public Security instructed Chinese college students to launch the "college teachers and students with the above network security class" online, inviting public security police officers and counselor representatives to establish and personal information protection and prevent telecommunications fraud The dimension jointly builds a open class for teachers and students across the country. From September 6th to 12th, teachers and students can log in to the official website of China University of China (dxs.moe.gov.cn) or WeChat code scanning video number, fast hand, B station to watch, the event is over, the course can be seen back.
Quiz

From September 6th to 12th, the Ideological and Political Work Department of the Ministry of Education and the Criminal Investigation Bureau of the Ministry of Public Security instructed Chinese college students to organize the "Guardian Youth Network with You" national college student network security knowledge answering activity, and popularized network security knowledge through online answers. Improve the ability of college students to prevent network fraud and use the network safely. Teachers and students can participate in answering questions through the "Chinese University Student Online" WeChat public account, click on the menu bar "Guardian Youth".
Cyber security has nothing to do with
Scholars, communicators, and guardians who do network security
It is the common responsibility of the whole society
Looking forward to your active participation!
Future / Phase / Essence / Color
Straight at the scene! Beilin University 2022 freshmen reported today!

The second day of the registration day! Hello, Beijing Forestry University!

New Yan Huanhuan! Did you find the surprise in Beilin University campus?

-bjfu1952-


Beijing Forestry University New Media Alliance
Produced | Beijing Forestry University Party Committee Propaganda Department
Illustration | 2022 National Network Security Propaganda Week official website
Source | Beijing Forestry University Party Committee Security Department (Office)
Author | Mao Chengzhi, Yang Qinrun, Geng Huimin, Wang Ziyu
Review | Cai Qingjie
School pair | Li Junwei
Editor -in -law | Zhang Wei
Review | Zhu Tianlei
Submit mailbox [email protected]

Set as an astrology every day, I don't miss it every day
For excellent Beilin people

Share+like 点+light 666 "watching"
- END -
Hengyang High -tech Zone: Juggi three innovations, support the "sunny sun" of the industry

The development of the park, industry -based, innovation as the soul.This year, th...
E -sports hotel efficiency upgrade sharp weapon -Huijie Technology Digital Platform

Gaming Hotel SaaSOn May 4th, Ctrip released the 2022 May Day holiday report displa...