Western Industry University was exposed to the real murderer by the Internet. What is the "specific invasion office office"?
Author:Xinmin Evening News Time:2022.09.06
The "Specific Invasion Office" is like a "digital channel worker" who follows the call. He has participated in the many secret operations of American intelligence agencies, and has been involved in the traditional spy activity from counter -terrorism and network attacks to traditional espionage activities.
Behind the scenes of Northwestern Polytechnical University suffered an overseas network attack, the black hands finally surfaced.
On September 5th, a survey report released by the National Computer Virus Emergency treatment Center and 360 Company showed that the Specific Invasion Action Office (TAO) under the National Security Agency (NSA) has implemented tens of thousands of malicious network targets in my country for many years Network attacks controlled related network devices and suspected of stealing high value data.
In response, the Chinese Ministry of Foreign Affairs responded that the US behavior seriously endangered China's national security and personal information security of citizens. China strongly condemned and asked the United States to explain and immediately stop illegal behavior.
What is this "specific invasion action office"?
Use a large number of network weapons
A statement in June of Western Institute of Technology aroused many attention. The statement states that there are fishing emails containing Trojan -horse procedures from overseas hackers and criminals, trying to steal relevant teachers and students' email data and personal information of citizens, and cause major risk hazards to the school's normal work and life order.
China National Computer Virus Emergency treatment Center and 360 Company jointly formed a technical team to conduct a comprehensive technical analysis of the case. According to preliminary judgment, the implementation of the network attack operation of the Western Technology University is the Specific Invasion Action Office (Code S32) departments under the Information Intelligence Intelligence Department of the National Security Agency (code S3).

Northwestern Polytechnical University was attacked by the Internet, and it was initially determined that the source of the Specific Invasion Action of the National Security Agency was initially judged. Picture source: GJ
The survey report shows that the United States has successively used 41 special network attack weapons and equipment to continue to attack theft of Western Engineering University, stealing core technical data such as the school's key network equipment configuration, network management data, and operation and maintenance data. Thirteen of attacks, as well as more than 60 contracts signed with US telecommunications operators by covering the company to build a network attack environment and more than 170 electronic documents.
The survey report also disclosed that the United States used a large number of online attack weapons to conduct secret hacking activities for leading enterprises, governments, universities, medical care, scientific research and other institutions in various industries in my country. In addition, the United States has long been listening to Chinese mobile phone users for a long time, illegally stealing the text message content of mobile phone users, and a wireless positioning.
Participate in many secrets
The "Specific Invasion Office" was established in 1998. It is currently a tactical implementation unit specializing in the US government specializing in large -scale network attacks on other countries. It consists of more than 2,000 soldiers and cultural personnel and set up 10 offices.
It is reported that the current person in charge of the "Specific Invasion Action Office" is Robert Joyce, graduated from Hopkins University, and entered the National Security Agency in 1989.

The National Security Agency (NSA) headquarters in Midori, Maryland, USA. Picture source: BusinessInsider
Historian Matthew Ed said that the "specific invasion office" is the "prodigy" of the American intelligence community, and the "acquisition that cannot be obtained" is a description of his duties within the department.
The "Specific Invasion Office" can access the intelligence goal of "the most difficult to be penetrated by spy technology" without discovery. The task is "through access to the global network, using computer network attacks as a part of military operations" Essence
Unlike traditional hacking activities, the attack of the "Specific Invasion Action Office" is more fine. It can manipulate, analyze and destroy any network communication and file transmission in normal network traffic. Water, electricity, gas and other people's livelihood facilities.
According to the US National Security Agency's information, the "specific invasion office" is like a "digital channel worker" who has followed the call, and has participated in the many secrets of the US intelligence agencies, from counter -terrorism and network attacks to traditional espionage activities.
According to public reports, the "Acting Office of Specific Invasion" also "made great achievements" in the process of chasing the "base" organization leader Ladan in the United States. Internal documents show that by tracking mobile phone calls, the department invades confidential communication channels among the "base" organization members, and collect information from mobile phones used by the "base" organization agents and other relevant personnel.
The name of the "Secret Empire"
For a long time, the American abuse of technological advantages and the implementation of large -scale, organizational, and non -differences around the world has been a veritable "secret empire".
Former US defense contractor Snowden exposed the large -scale network monitoring scandal of the US government in 2013: the Global Secret Supervision Project codenamed the "Prism" codenamed by the National Security Administration, and monitoring monitoring such as e -mail, Google chat, and online telephone. In addition, the United States has implemented no different monitoring and listening, from competitors to ally, and even the American people, all within the scope of monitoring.
Chinese Foreign Ministry spokesman Mao Ning responded to Western Workers' Internet attacks on the 5th.She said this case once again shows the extreme importance of maintaining national network security.As the main victims of hacking, China has resolutely opposed any form of cyber attacks.Chinese law clearly stipulates that any network invasion and damage to the information system are prohibited.Mao Ning emphasized that the threat of network space security is a common challenge facing countries, and maintaining network security is the common responsibility of the international community.China adheres to the use of network space peacefully, is willing to work with the international community, strengthen dialogue and cooperation, jointly oppose network hegemony, jointly respond to various types of network attacks, maintain peace, security, openness, cooperation, and orderly network space, promote the establishment of multilateral and democracyThe transparent global Internet governance system will work together to build a community of fate of the network space.
Produced deep -sea district studio
Written Wang Ruoxian
Edit deep sea otter
- END -
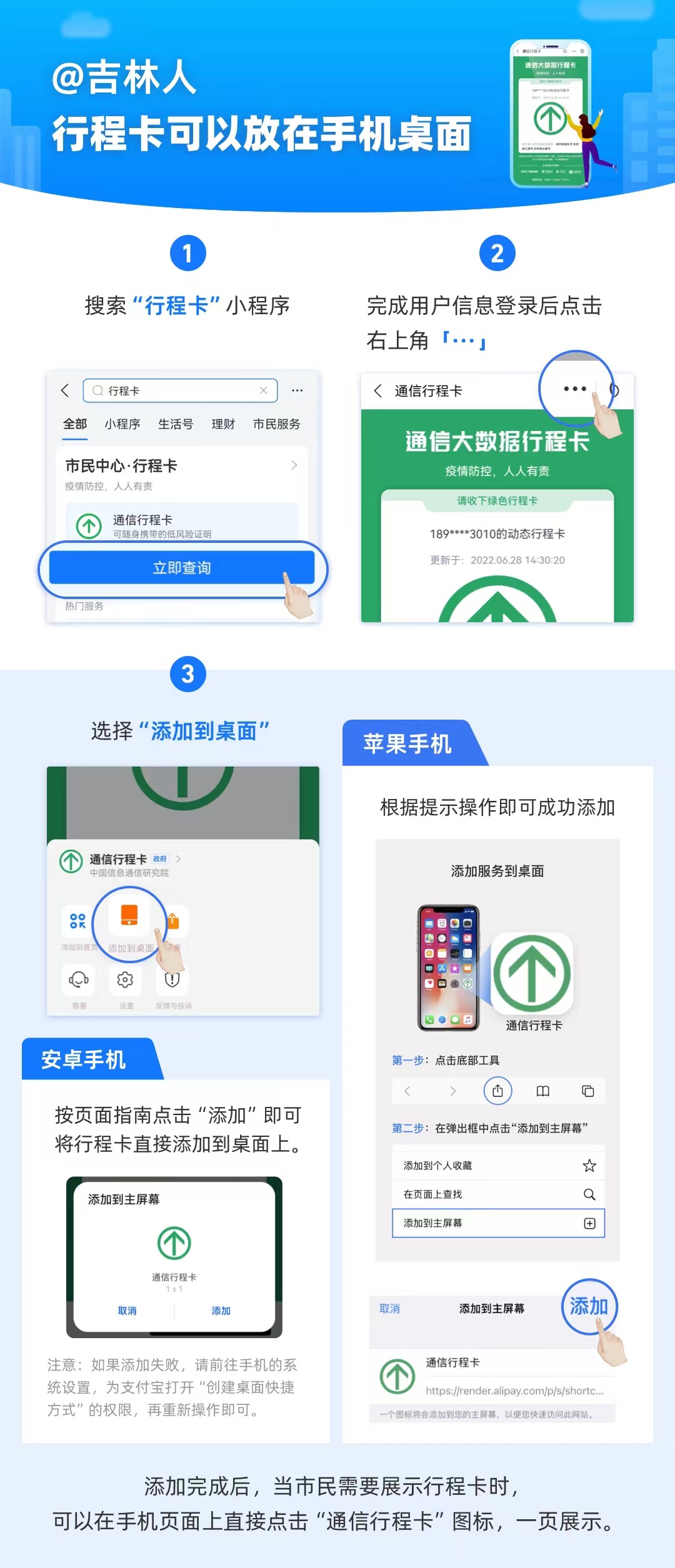
The itinerary can be displayed on the phone desktop, which is too convenient!
Recently, there have been no new local diagnosis cases in our province for many da...
"China Business Daily": The three major kung fu of digital economy, serving the people's livelihood, and improving urban management Tianjin digital development

Interview with the Deputy Minister of the Propaganda Department of the Tianjin Mun...