"See" safety risk, the digital era requires a Chinese plan
Author:Chang'an Street Knowledge Time:2022.08.01

The digital economy is becoming a powerful driving force for the new round of industrial changes. In the face of the challenges brought by the rapid development of digital technology and digital scenarios, seeing security risks has become the foundation of the development of the digital economy. In recent years, network security has accompanied the development of digitalization and continuous expansion of connotation and extension. Traditional network security has been upgraded to digital security.
On July 30, the opening ceremony of the 2022 Global Digital Economic Conference Digital Security Summit and the 10th Internet Security Conference was held in Beijing. The conference was hosted by the Organizing Committee of the Global Digital Economic Conference, and was hosted by the Beijing Economic and Information Technology Bureau, the People's Government of Chaoyang District, Beijing, and 360 Group. Power builds a digital security barrier system for the country and escort the digital economy development.
At the opening ceremony of the conference, Zhou Hongyi, the founder of 360 Group, delivered a keynote speech on "360 as the Digital Security Age of Digital Security". He pointed out that in the face of strong opponents, "invisible" has become the biggest pain point in the digital security era. For digital transformation companies, "seeing" is a safe watershed, avoiding "seeing" talking about safety is itching.

Since entering the digital era, major changes have taken place in digital security compared to the past network security. Zhou Hongyi pointed out in the opening ceremony that the first change was that the inner vulnerability of digitalization caused greater security risks. Digitalization has four characteristics, that is, everything can be programmed, everything needs to be interconnected, big data -driven business, and intelligent liberation of productivity. The essence is the software definition world. However, this also means that risk is faster in virtual and reality, scenes and scenes. A attack may have an impact on the world. In addition, the higher the degree of intelligence and automation, the lower the role of people can play and keep the bottom line. The second change is the continuous upgrade of external threats. In the past, security threats were upgraded to professional network criminal organizations. Its technical capabilities were no less than security companies. Ratch attacks, mining attacks, supply chain attacks, DDOS attacks, website attacks, and they were familiar.
Cyber security is upgrading to digital security, and the problem of new eras should be solved with new weapons. At the national level, in recent years, the relevant policies and regulations of data security have continued to improve. In September 2021, the Data Security Law of the People's Republic of China was officially implemented, and all "data processing activities" of data collection, storage, use, processing, transmission, provision, and publicization were included in the scope of standardization. Entering 2022, various localities have introduced management measures and policies related to data security. Starting on September 1, 2022, the "Evaluation Measures for Data Outbound Security" was officially implemented, which standardized data outbound activities and promoted data cross -border security and free flow. In addition, the "Regulations on Network Data Security" is also included in the legislative work plan of the State Council this year.
At the level of enterprise, related enterprises of network security also quickly upgraded themselves in the era of digital and high -speed development, and found a suitable development plan. The 360 Group has invested 20 billion yuan in the past 20 years, gathered 2,000 security experts, accumulated 2000PB security big data, and established a set of safety operation service system with "seeing" core, forming a set of "perceived risks, perception risks, perception, risk, See the security ability of threats and resistance ". In this regard, Zhou Hongyi said: "The core of this framework is not selling products to customers, but to help customers build a set of safety operation systems with 'see' as the core, which is essentially service."
Zhou Hongyi pointed out that well -known security companies worldwide are TOC. These companies have massive end users, have the ability to analyze the entire network cloud and big data, do not pile up products, and provide security capabilities in the form of service. This is the result of full competition and also represents a safe future. In China, the 360 Group is taking this road.

In Zhou Hongyi's view, the 360 Group explores the Chinese plan in the digital security era. After entering the digital age, traditional industries and government departments and cities are the protagonists of digitalization. The 360 Group will focus on security, with the strategy of "going up the mountain and the sea to help small", and use digital security services to help digital China construction.
Among them, "up the mountain" is the problem of the high mountain of technology, focusing on helping the country to solve the problem of digital security. The 360 Group centered on "seeing" and helped the country to create a set of "radar" and "early warning aircraft" of digital space. After 99%of the national network attacks were discovered independently by 360. Since then, the 360 Group has used the capabilities to serve the country to serve government -enterprise customers, small and medium -sized enterprises, and in order to guard the national digital security and assist government and enterprises to protect strategic asset security.
"Go to the Sea" is a digital blue ocean, refining the capacity framework of serving the country, copying it to the city, and copying it to all walks of life, including the use of SaaS models for free to use it to small and medium -sized enterprises to help the digital development of the industry. The safety risks facing government departments, cities and enterprises are also being upgraded. They are no longer hackers, but have professional capacity cyber crimes. The 360 Group uses "seeing" as its core to refine the capability system based on TOC and TON into a digital security brain framework, reinterpret security, and enter the TOB market.
"This year I set a OKR for myself to allow small and medium -sized enterprises to enjoy national digital security services." Zhou Hongyi said in the opening ceremony.
Data-nickName = "Chang'an Street Know" Data-ALIAS = "CapitalNews" Data-Signature = "provides reliable political analysis, interprets the details of the news that you can't pay attention, and the brain supplement is interesting and political common sense. A group of editors close to the core editor., Provide you with the news of current political affairs. "Data-from =" 0 " />

- END -
Announce the technical factors of the success of the Internet
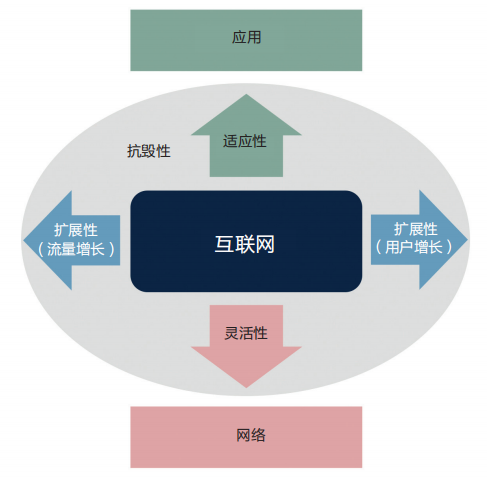
Although the success of the Internet is undeniable, the success of the Internet sh...
Optimize the business environment 丨 Changzhi High -tech Zone: The electronic information industry "wind and water"

The electronic information industry of Changzhi High -tech Zone winds and water ri...