Jiu Gua | How to prevent and control new "running money laundering" under digitalization?
Author:Jiu Gua Financial Circle Time:2022.06.26
Author | Cheng Yuanhong Jinchi Cheng Peizhe Lu Boliang (Business R & D Center of Industrial and Commercial Bank of China)
Source | China Financial Computer
Edit | Wu Wen Zhang Yundi
Beauty | Yang Wenhua

In order to cover up the characteristics of money laundering and avoid supervision blows, criminals continue to upgrade the means of money laundering, and rely on the QR code to "run money laundering" based on the third -party payment platform ...
With the acceleration of digital transformation, the threat of black production attacks facing the financial industry has also been upgraded. In response to the cooperation between banks such as e -commerce shopping and ETC, the black -produced personnel have designed different fraud words. The scene is strong and directed, making it difficult for ordinary users to distinguish between authenticity. Although the new types of fraud have emerged endlessly, the changes are inseparable. Money laundering and sales are still the core link of the criminal activity of the black industry chain. The crackdown and traceability of the money laundering link is an important breakthrough to crack down on black production.
In order to effectively block the key chain of fraud -related crimes, the public security organs continue to carry out special strike activities such as "broken cards" and "net nets", and financial regulatory agencies have also successively introduced a series of policies such as "Anti -Money Laundering and Anti -Terrorism Financing Supervision and Administration Measures" such as financial institutions Documents strictly control the flow of money laundering.
In order to cover up the characteristics of money laundering and avoid supervision blows, criminals continue to upgrade the means of money laundering, and rely on the QR code "running money laundering" by the third -party payment platform. This new money laundering method through third -party payment institutions is more hidden, which greatly reduces the threshold for money laundering. In order to ensure the security of customers' funds, the ICBC Safety Offensive and Defense Labs carried out special research on "running money laundering" in black production. This article mainly introduces the current development trend of black -yield money laundering and the new method of "running money laundering", and puts forward suggestions from technical levels.

1. The development trend of black -producing money laundering
Black -made money laundering has gone through a gradual development process from scratch and from small to more. Looking at the history of money laundering, money laundering is often inseparable from illegal financing and gambling. The following are several typical money laundering methods.
1. "Underground Capital Villa"
The "Underground Capital Village" is laundering through the "two funds pools". The domestic and overseas funds are fully divided, and each cycle. From the book, there is no foreign exchange transaction behavior. The actual transaction has been completed through "knocking". When the criminals report the price of the imported equipment or raw materials when the cargo is imported, obtain rebates and stolen money from foreign suppliers, and retain illegal income abroad; The method of transaction amount is deposited from foreign importers into an exporter's account abroad.
2. Casino chips
In order to legalize illegal income, illegal elements are gambled at the bargaining chips equivalent to illegal income at legal casinos, and usually bet on both sides through the size of gambling. After the chips are converted into gambling income, the criminals require the casino to remit cash on cash. To your account. When the judicial organs launch the procedure of anti -money laundering investigation of the suspects, they usually defend themselves on the grounds that "gambling in legal casino", and the legal casinos are protected by law and strictly prohibit the leakage of customer information to any third party. Within a limited time and cost range, it is difficult for judicial organs to obtain sufficient evidence to prove that the illegal income of criminals is not obtained by gambling.
2. "Running Money Laundering" method and characteristics
In recent years, with the use and promotion of new technologies such as artificial intelligence and big data analysis in the field of anti -fraud and anti -money laundering fields, traditional black -producing money laundering methods have been effectively curbed. In order to avoid the risk control and interception of financial institutions, a new money laundering method called "QR code running points" (hereinafter referred to as "running points") gradually spread between the black production team.
Running points are a new type of money laundering model that uses WeChat payment and Alipay and other two -dimensional code payment platforms. Gambling and fraud gangs collect a large number of two -dimensional codes of normal users, hiding gambling funds and fraud in normal funds, thereby avoiding regulatory blows.
Compared with the traditional way of money laundering, the hidden score is stronger, which brings greater challenges to anti -money laundering supervision. "Running money laundering" generally shows the three major characteristics of channels and scene transfer, generalization of participants, and online expansion of the gang.
1. Money laundering position transfer from bank to third -party payment platform
Traditional money laundering is mainly based on bank cards, and transfers and payment operations through mobile banking, online banking and other channels. After many years of accumulation, financial institutions have deployed a large number of anti -money -laundering and risk control models to intercept the flow of abnormal funds. Criminals then turn their eyes to their eyes to turn their eyes to their sights Third -party payment platform. In terms of anti -money laundering experience and model construction, the Internet payment platform has a certain gap with financial institutions such as large commercial banks, providing a living space for "running money laundering". Black -made personnel maliciously transferred funds to the Internet payment platform, causing bank -side funds to flow to data, so they cannot effectively block the money laundering capital flow.
2. Money laundry participants present generalization and concealment characteristics
The traditional anti -money laundering core work is mainly aimed at the internal personnel of the black production. Due to the limited number of black producers and resources in the past, the effect of governance through risk control protection, traceability strikes and other means is more significant. However, with the further increase of regulatory efforts, the money laundering methods of black production have also been further concealed. In order to escape the risk control model, the black production personnel packaged the "running money laundering" activity as part -time job, and attracted ordinary people to participate in running points with titles such as "student part -time" and "high -paying day knot", which made a lot of in running score activities. Participation of non -professional black producers. Because the running accounts used by these runners are often the bank card accounts used in their daily life, which contains normal transaction records such as wages and consumption, which further increases the difficulty of identification and prevention and control of anti -money laundering. 3. Quickly expand through online ways
Traditional money laundering gangs recruit personnel through offline methods. The recruitment costs are high and the scale of expansion is limited. Members have a certain social or relative relationship between members, and their regional characteristics are more obvious and they are easily arrested by traceability. The running operating mechanism breaks through the recruitment restrictions of traditional offline money laundering. With the help of various social platforms, dark webs and other channels, it is necessary to solicit runners. You only need to provide QR code pictures online to complete the formation of money laundering gangs. faster. At the same time, the running personnel are connected by a single line through anonymous encryption chat software, which is very difficult to trace the entire gang. Therefore, the scale of running gangs is very easy to expand online quickly, and it is difficult to trace the source.
3. ICBC's "running money laundering"
Thinking and countermeasures
Traditional anti -money laundering methods can no longer effectively ensure the fraud from corporates and users from criminals. To this end, the ICBC Safety Offensive and Defense Laboratory has proposed countermeasures from accounts, transactions, equipment and other dimensions, so as to prevent and control new money laundering risks more effectively Essence
1. Account dimension: knowledge map
In the past, the judgment of money laundering was often based on the analysis of trading behavior and previous historical experience in the past, but now the running staff uses a bank card with normal consumption records. From the perspective of the transaction dimension, it is difficult to complete the money laundering transaction. Account judgment leads to a lag of judgment. And too tough rules and list judgment methods inevitably affect the experience of normal customers, triggering unnecessary complaints and other issues.
To solve the above problems, ICBC introduced knowledge map technology. In the field of anti -money laundering, the characteristics of customer transaction objects, equipment, IPs used, and IP are aggregated through knowledge map technology, and a bank card account with a strong correlation after aggregation will be associated to achieve risk early warning before the occurrence of money laundering transactions. The money laundering transactions have the characteristics of "fast forward and fast out", showing a trend of large amounts to small -scale transfer. Once the funds are included, they will be transferred through transfer, consumption, etc., and the transaction IP often changes. According to the analysis of the knowledge map of the ICBC, the average daily suspicious IP address can be associated with 7053, involving 2,836 risk accounts. By establishing a black and gray list mechanism for the recognized risk account, it can achieve the unprecedented criminals in the black producer gang in advance. Early warning to avoid further loss of customer funds.
2. Trading dimension: federal learning
The accuracy of machine learning depends on the number of valid samples. Commercial banks simply rely on their own data to hardly complete the training of risk control models, and must be improved with the help of industry data. In the current environment of data, assets, for the consideration of industry competition and privacy security, data between different institutions is difficult to achieve comprehensive sharing. The criminals know this well, so you will choose to use the accounts of different banks or third -party payment accounts to cross -bank and cross -institutional payment, resulting in each institution can only pursue consumer records and clues preserved in the institution, but it is difficult to track the closed loop of the entire transaction. Essence
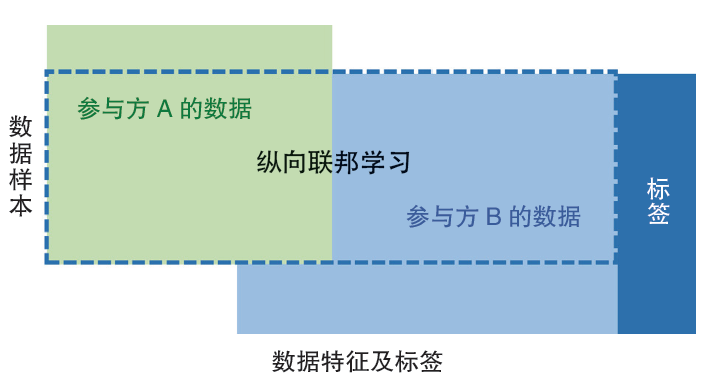
To solve the above pain points, ICBC tried to introduce federal learning technology. Using the vertical federal learning model (as shown in Figure 1), the data islands existing between banks and Internet financial companies and social media have been opened to improve the trading chain and effectively summarized the characteristics of money laundering. Training with data provided by two or more institutions, these data will only be used as model parameters, which will not cause privacy leakage problems. ICBC uses federal learning technology to explore the electronic bank fraud account recognition model of cross -financial institutions. The prototype of algorithm proves that using federal learning technology to ensure that the data is not available in the local data, Effectiveness increases the accuracy of the co -construction model by 38.3%compared with the independent model, an increase of 28.9%accuracy, and a recall rate of 37.2%. The co -construction model can clearly outline the entire trading chain of the criminals, so that it has nothing to do with money laundering.
Figure 1 Vertical Federal Learning Model
3. Equipment dimension: device fingerprint
The emerging money laundering gang no longer needs to convene running staff to arrive at the scene. Just install the remote control app for the runner's mobile phone to obtain information such as the online banking message verification code of the runner. Account, realize the money laundering of scripts. There is no social relationship between the running staff, and the bank account used has no regional correlation.
In response to this discrete personnel distribution, ICBC uses equipment fingerprint technology to lock the black -related equipment used by criminals, and achieves positioning of black accounts through the tracking of black -related equipment. Equipment fingerprint technology can collect the client equipment multiple dimensions feature information, upload it to the background server, and then generate the unique ID for each customer device by random algorithm. Figure 2 is an example of a simple device fingerprint generation example Essence Figure 2 Device Fingerprint Generation Example
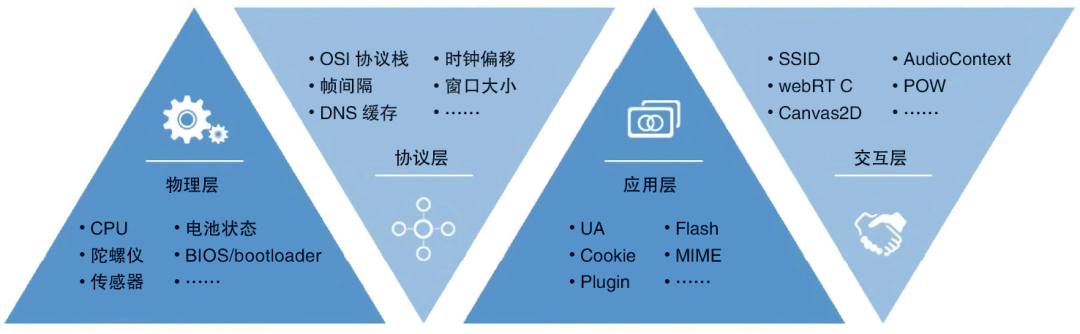
Both the Android and iOS systems have APIs that can be called by developers to obtain the client -related software and hardware information. Although the black -gray production institution will bypass these APIs by flashing or virtual machines, they can consider multiple dimensions. The collection of software and hardware information to avoid these forged behaviors. Figure 3 is a simple example of collecting multi -dimensional information to generate equipment fingerprints. This information varies from device. The device fingerprints generate completely independent device ID through part of the differential information.
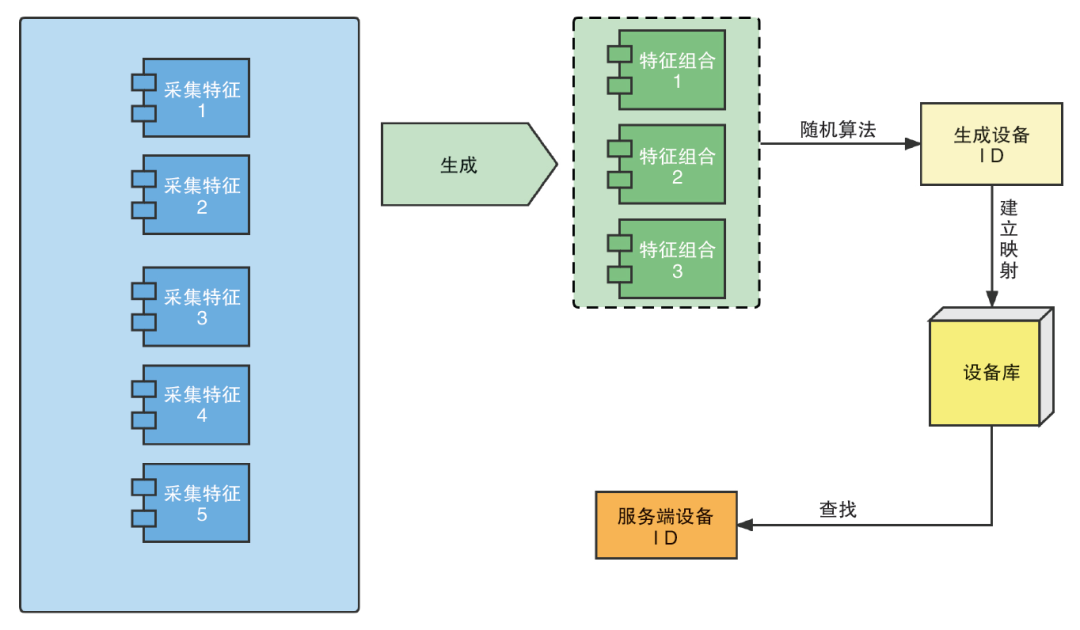
Figure 3 Collection of multi -dimensional information generation equipment fingerprint example
In the process of running, the criminals will usually not be used immediately after logging in to online banking. Instead, they will confirm the availability of bank cards through multiple small payments (such as WeChat red envelopes, Alipay transfer, etc.). We call it " Silent period. After ensuring that the bank account can be used normally, the criminals will transfer large funds to the transfer operation. Relying on equipment fingerprint technology, ICBC generates 36 risk labels through more than 70 features of the equipment. If the account is detected in the "silent period", the account is logged on on the black equipment, which can be pulled into the ash list for control; When the account proposes a large amount to transfer to the application, the transaction can be blocked and frozen the bank card to avoid further capital losses.
The above three technical ideas that cope with "running for money laundering" have been tried and practiced in the real confrontation process with the black production. Based on the "running money laundering" account as the source of analysis, connect data from the dimensions such as equipment, transactions, communication, and networks to tap the characteristics of fraud accounts. Expand the scope of anti -money laundering analysis horizontally, deepen the depth of the money laundering gang vertically, start with the transfers, payment and other links, and identify the complete money laundering chain through association analysis, sort out the organizational context and time and space trajectory of the gang, thereby enhancing the traceability ability of the hidden traces of the fraud gang network network , Empower business for fraud account recognition. ICBC piloted some provinces with a relatively high incidence of "running money and laundering", and achieved a 56%decrease of the account involved in the month of the month. From the source to strengthen the interception of gambling and fraud funds, it has made important contributions to maintaining financial security. Highly evaluation of territorial regulatory agencies.
The money laundering scene has become the main battlefield of the financial industry and the black production game. Banks are the forefront of anti -money laundering work. ICBC Safety Offensive and Defense Lab will continue to pay attention to the latest trends of black production, strengthen anti -money laundering technology research, and strive to achieve abnormal capital flow. It is found in advance that it can effectively prevent and crack down on money laundering crimes, and contribute to maintaining national economic and financial order and ensuring the stable development of society.
This article was published in "China Financial Computer", No. 6, 2022
- END -
"Heze City Implementation and Implementation of the Provincial" Steady Progressive "high -quality development policy list division of labor"
In order to implement the list of high -quality development policies (the first, second, and third batch) issued by the provincial government's Shandong Province in 2022 in Shandong Province in 2022...
Chongqing: The lowest down payment for the first house of the provident fund deposit employee family
Zhongxin Jingwei, June 15th. On the 15th of the Chongqing Municipal People's Government website, Chongqing released the Several Measures for Chongqing to Promote the Patient Circle and Healthy Develo...